SoftPerfect Network Scanner
Online User Manual
Getting started
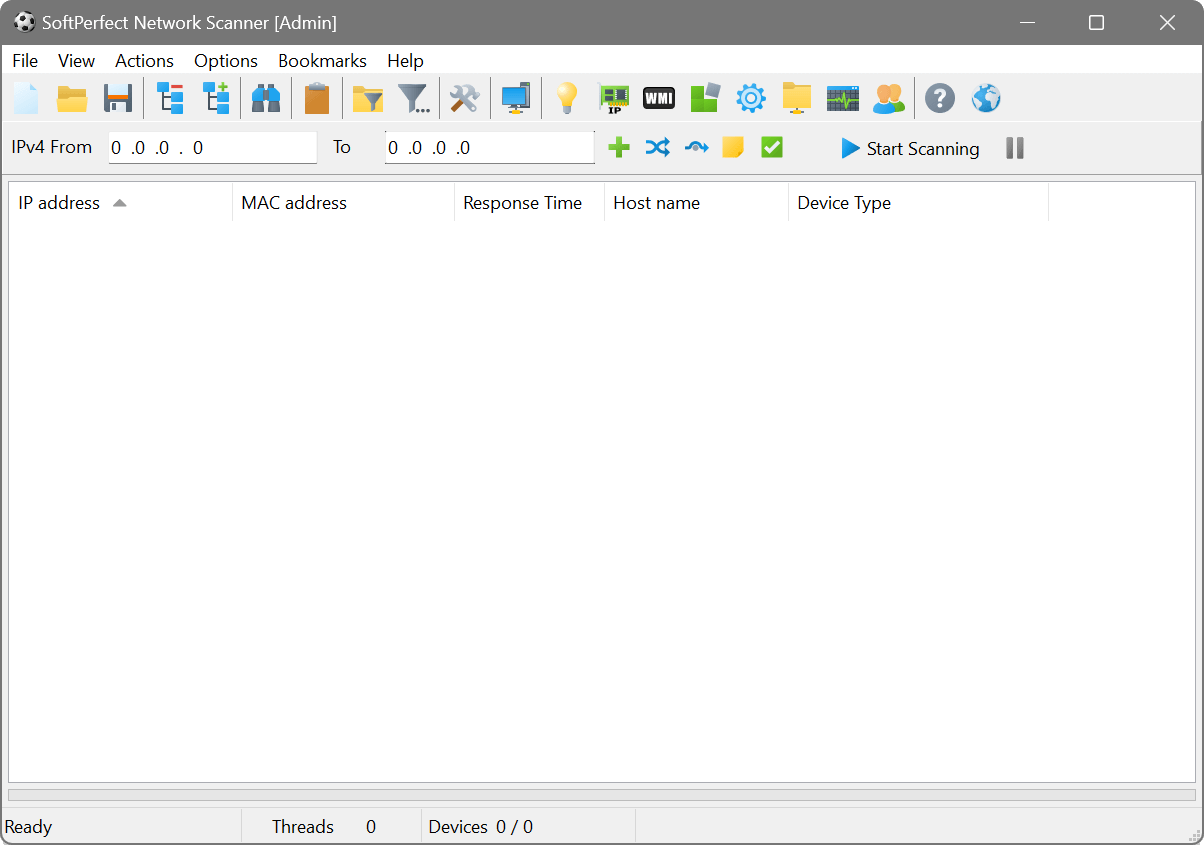
Under the menu there is a toolbar with buttons used to access the main features.
The program controls are as follows:
| Clear the display | |
| Load the scan results from a XML file | |
| Save the scan results to a file | |
| Collapse the results tree | |
| Expand the results tree | |
| Search the results tree | |
| Paste IP address from the clipboard | |
| Apply the shares filter. Only devices with available shared folders are shown | |
| Open the advanced filter panel | |
| Program options | |
| Discover DHCP servers | |
| Open the Wake-on-LAN manager | |
| Automatically detect the network configuration | |
| Open the Windows Management Instrumentation manager | |
| Open the remote registry query manager | |
| Open the remote service query manager | |
| Open the remote file query manager | |
| Open the SNMP query manager | |
| Open the remote groups query manager | |
| Online Help (this web page) | |
| Add one or more IP address range to scan | |
| Convert a CIDR notation to a range, and vice versa | |
| Toggle noncontiguous scan mode | |
| View or set a comment assigned to the IP address range |
Application options
Press Ctrl+O or the Options button ![]() to access the Network Scanner options:
to access the Network Scanner options:
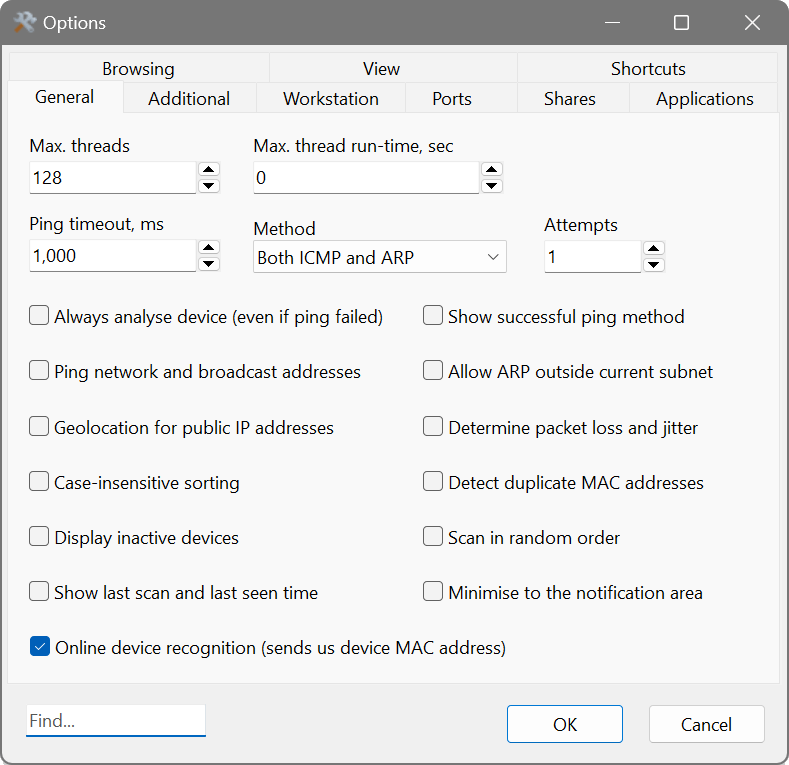
On the General tab:
- Max. threads: the maximum number of scanning threads.
- Max. thread run-time gracefully stops a thread and moves on to a next IP address if it has not finished within the specified time. If the thread cannot be stopped, it will be forcibly terminated when 2 x the specified time elapses. A zero run-time sets no limit on thread execution time.
- Ping timeout: the period to wait for a reply from the remote device.
- Method: the ping method. Can be chosen from ICMP (ping), ARP (arping), or both.
- Attempts: the maximum number of ping requests.
- Always analyse device (even if ping failed) forces the scanner to analyse a non-responding host.
- Ping network and broadcast addresses: when enabled, the scanner tries to ping the first and last IP addresses in a network.
- Geolocation for public IP addresses displays the city and country of public IPs.
- Case-insensitive sorting ignores case type when results are sorted.
- Display inactive devices adds non-responding hosts to the results.
- Show last scan and last seen time displays the time when the host was last scanned and when it was last seen online.
- Show successful ping method displays the ping method that resulted in receiving a response.
- Allow ARP outside current subnet: normally ARP requests are not sent when scanning IP addresses outside the current subnet. However, if your router runs proxy ARP or forwards ARP requests and responses, turning this option on may help detect more devices and their MAC addresses.
- Determine packet loss and jitter sends a series of echo requests and shows the number of lost packets as well as a packet delay variation. The higher are the numbers, the less reliable the connection is.
- Detect duplicate MAC addresses informs you if there are any duplicate MAC addresses discovered.
- Scan in random order scans IP addresses and ports in a random order, not sequentially.
- Minimise to the notification area: the application will be minimised to the system tray.
- Online device recognition: when enabled the scanner will determine the device type, brand and model where possible.
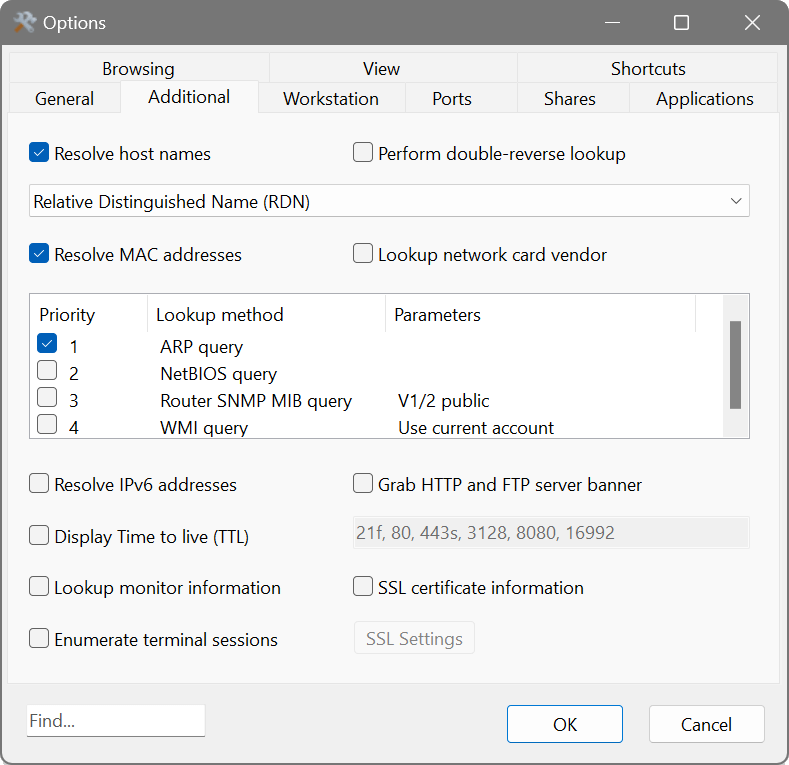
On the Additional tab:
- Resolve host names: when enabled, the IP addresses are converted to the host names.
- Perform double-reverse lookup: convert the resolved host names back to their IP addresses.
- Resolve MAC addresses: when enabled, you will see hardware (MAC) addresses. There are four discovery methods available for address resolution in local or non-local subnets:
- The ARP query method sends an ARP packet to the target device to resolve its MAC address directly.
- Similarly, the NetBios query method sends a NetBios packet to the target device. If the target device responds to the request, the response will contain the MAC address of that device.
- The WMI query method connects to the WMI subsystem on the target computer and analyses the Win32_NetworkAdapterConfiguration class to find out its MAC address.
- The Router SNMP MIB query method works differently. Before starting scanning, the application sends a few SNMP requests to the default gateway configured in your network card’s properties in order to determine which MAC address corresponds to which IP address. If the gateway is SNMP-capable and responds to the request, the application will cache this information and use it for MAC address resolution.
Generally, the ARP query method is sufficient to resolve all MAC addresses in a local subnet. However, if you also need to discover those behind the router, enable the NetBios query and Router SNMP MIB query methods and place them first and second in the list. Double-click a method to access its additional configuration parameters.
- Lookup network card vendor: as per the IEEE standard, the first three octets of a MAC address represent the NIC’s vendor. Enabling this option will try to resolve the name of the network card manufacturer, which may or may not match the device brand name.
- Resolve IPv6 addresses enables the Network Scanner to obtain the IPv6 address of a remote host. This feature discovers addresses of hosts with a dual IPv4/IPv6 stack.
- Display Time to Live (TTL) displays the time to live (TTL, also known as hop limit) in ping ICMP responses.
- Lookup monitor information displays monitor vendor, model and serial number if available. This feature requires the remote registry service, as the information is read from the registry.
- Enumerate terminal sessions displays all connected users on a terminal server and their origin.
- Grab HTTP and FTP server banner displays web-server and file server software name and version if one is running on a remote host. To probe an FTP port, append f to a port number, for example 21f. For an HTTPS probe, append s, for example 443s. A port number without a suffix does a standard HTTP probe.
- SSL certificate information displays SSL certificate details on devices with open port 443.
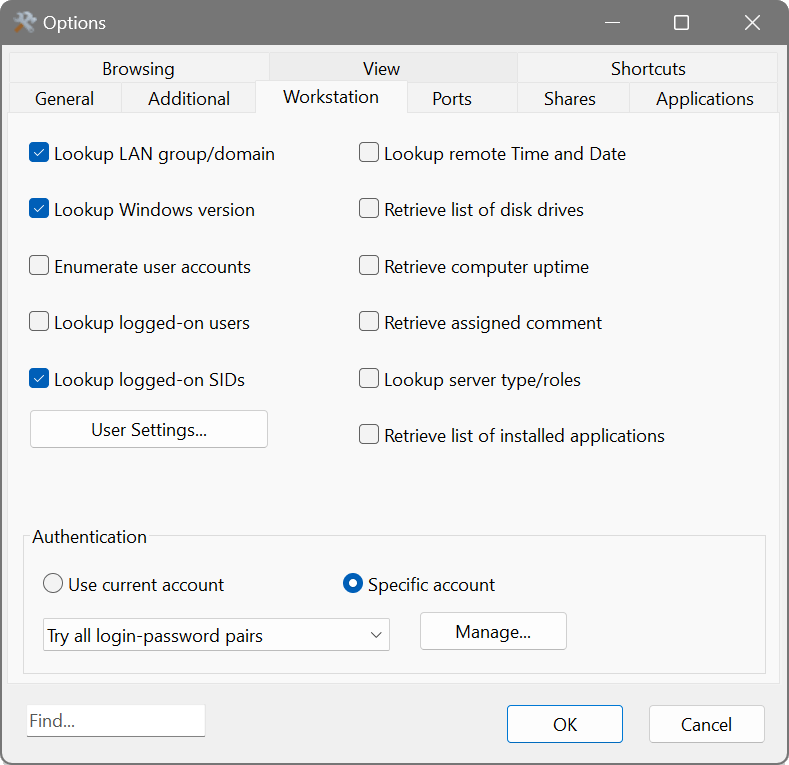
On the Workstation tab:
- Lookup LAN group/domain displays the workgroup/domain name that a Windows workstation belongs to.
- Lookup Windows version displays the Windows version on a workstation.
- Enumerate user accounts lists all user accounts registered on a remote computer.
- Lookup logged-on users displays a list of users currently logged-on to a Windows workstation.
- Lookup logged-on SIDs displays Security Identifiers of the users currently logged-on to a Windows workstation.
- Lookup remote Time and Date retrieves and shows the time of the day on a remote system.
- Retrieve list of disk drives lists all disk drives available on a remote computer.
- Retrieve computer uptime shows how long a remote computer was up and running.
- Retrieve assigned comment displays a comment assigned to a Windows workstation.
- Lookup server type/roles displays all roles (e.g. PDC, SQL server, Master Browser) assigned to a server.
- Retrieve list of installed applications displays installed applications from a remote computer.
On the Ports tab:
- Check for open TCP ports attempts connection to the specified TCP ports and reports those open (you can specify several ports separated by a comma or dash, e.g. 21, 80, 110-115).
- Check for open UDP ports discovers some UDP-based services such as DNS, TFTP, NTP, NBNS, MSSQL and RADIUS.
See the rightmost columns on the main screen once you have enabled one or more options.
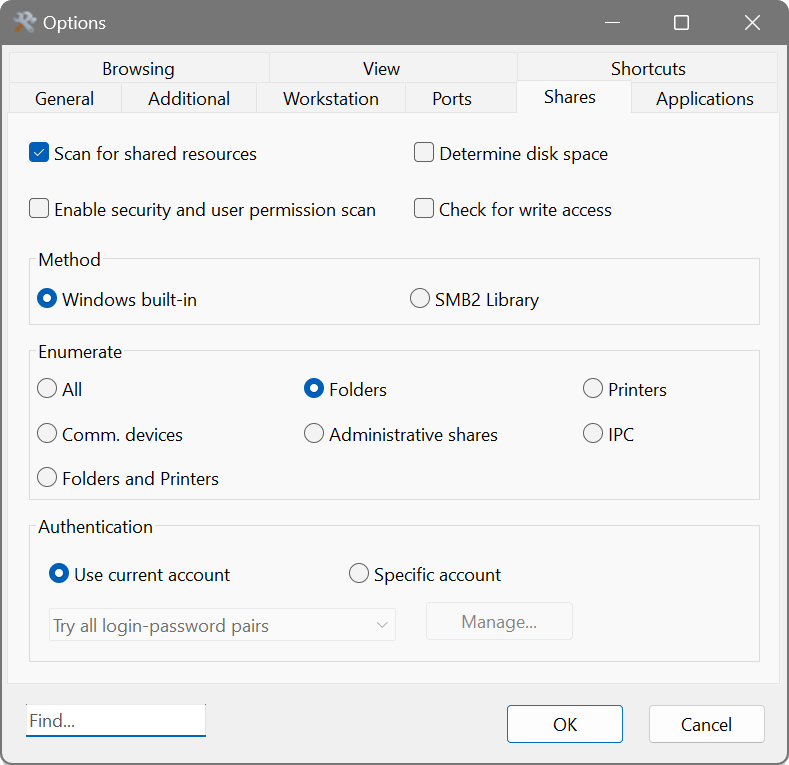
On the Shares tab:
- Scan for shared resources enables scanning of shared resources. All the possible types of shared resources are listed below.
- Enable security and user permission scan: with this option enabled, the Network Scanner will discover what reading and writing privileges are assigned to shared folders. You may have to be an administrator to retrieve this information.
- Determine disk space determines shared folders’ total and free space.
- Check for write access determines whether the shared folder is writable or read-only.
- All: all resources.
- Folders: shared folders or drives.
- Printers: shared printers.
- Comm. device: communication devices.
- Administrative shares: special share reserved for remote administration of the server, e.g. ADMIN$, C$, D$, E$, etc.
- IPC: interprocess communication (IPC).
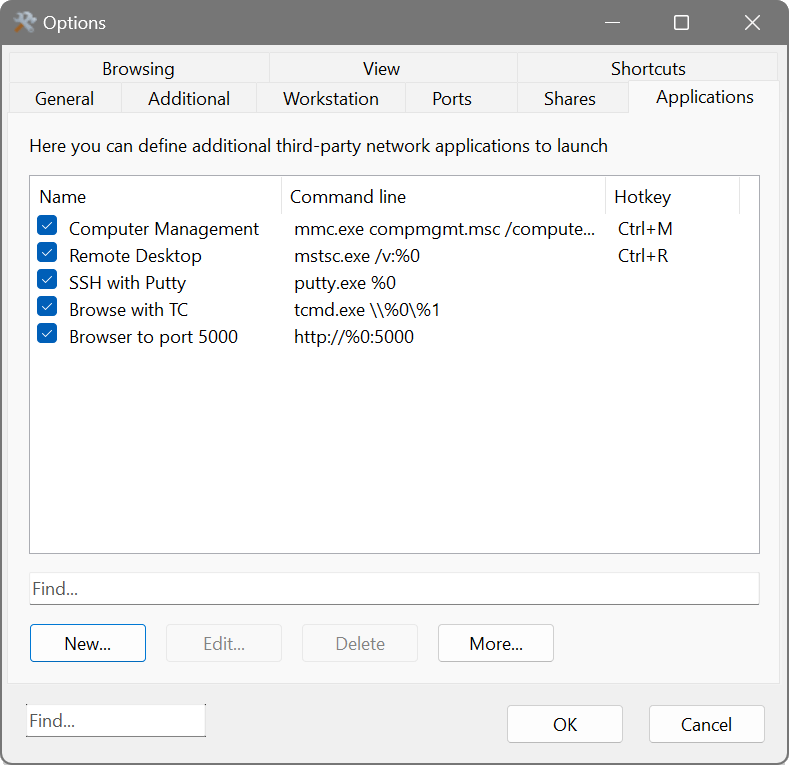
The Applications tab extends support for third-party applications. For example, if you use remote administration or specific network client software, you can setup the Network Scanner to connect to a remote host using the additional software directly from the Network Scanner:
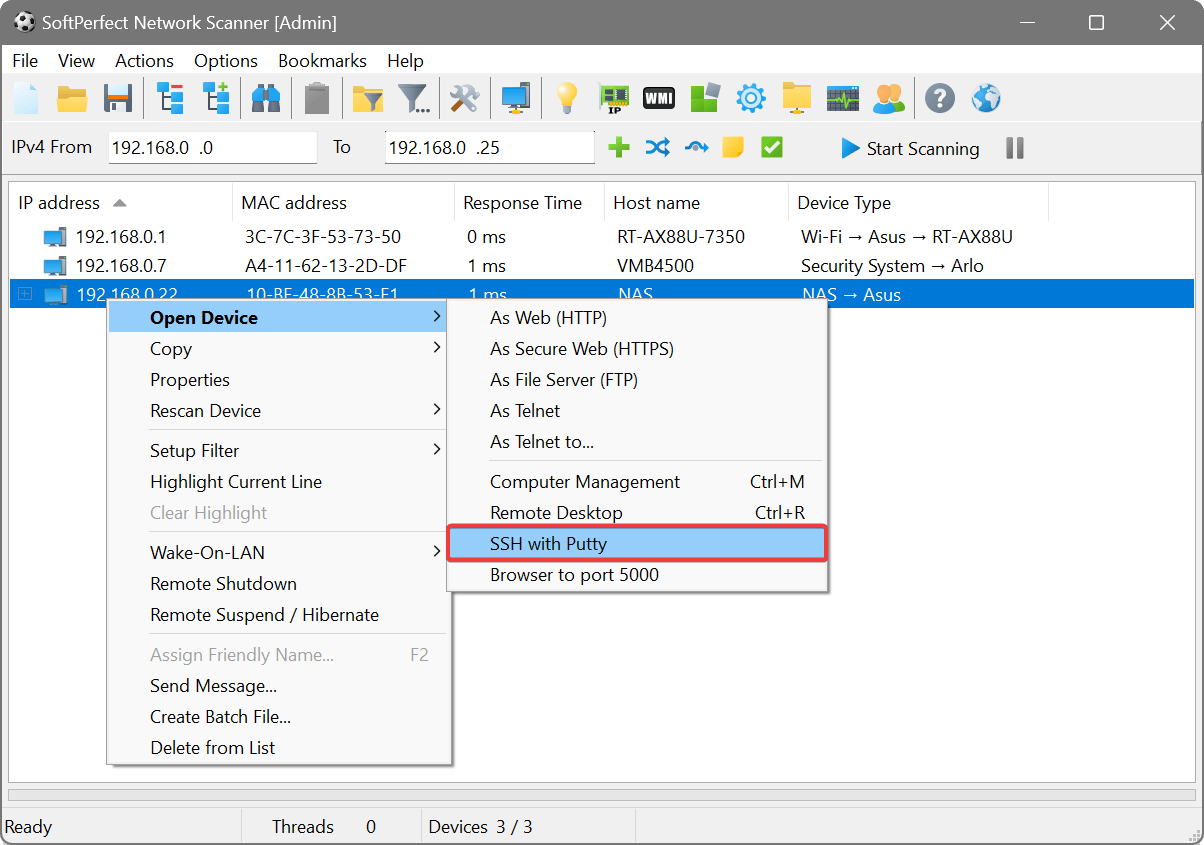
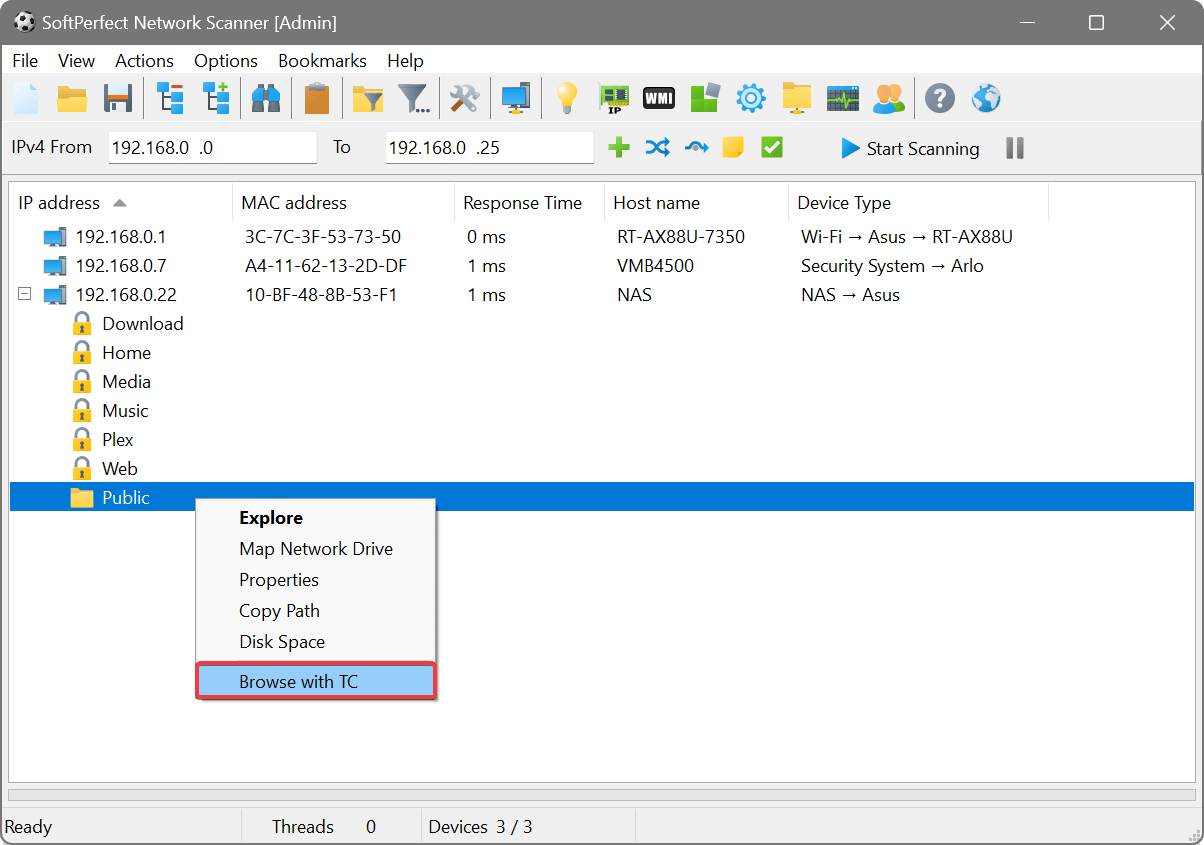
Should you require to pass extra arguments upon launching an application, you can use user-prompted parameters specified in braces. It is also possible to specify a default value after a colon. If the parameter name contains the “file” or “path” string, there will be a button allowing you to choose a file or a directory respectively. As an example, the following line lets you quickly execute commands on the remote system with PsExec:
psexec.exe \\%0 -u {User name:Admin} -p {Password} {Command}
Launching this command will bring up a window where you can specify the arguments to pass to PsExec as shown below. Then the Network Scanner will launch PsExec with your input.
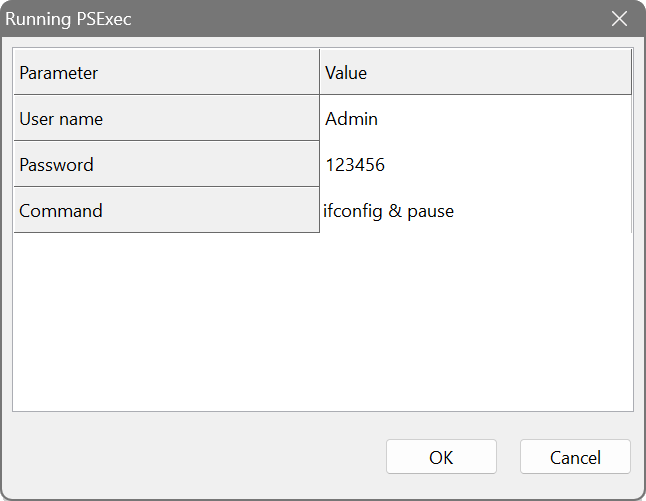
Since the Network Scanner interprets braces as user-prompted parameters, you may have problems with passing a value containing braces, for example a GUID. In this case double the braces, e.g. myapp.exe {{12345678-ABCD-EFGH-1234-567890ABCDEF}}, so that this value is not treated as a user-prompted parameter.
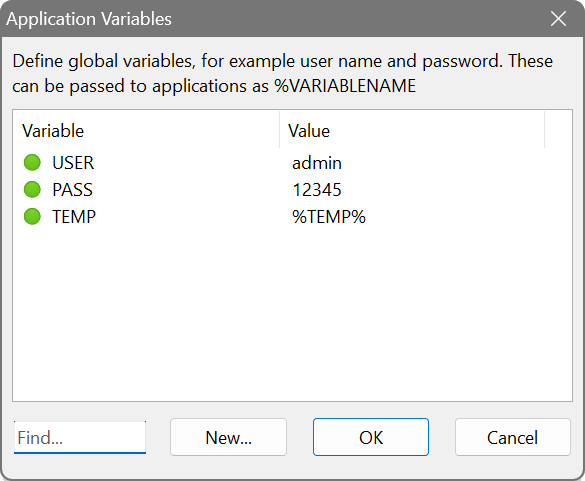
If you have got many applications to launch and some require common parameters such as a user name and password, you can define these as global variables. Click More... on the Applications tab and then choose Variables. A value can be either plain text or an environment variable, whose contents you can pass to applications.
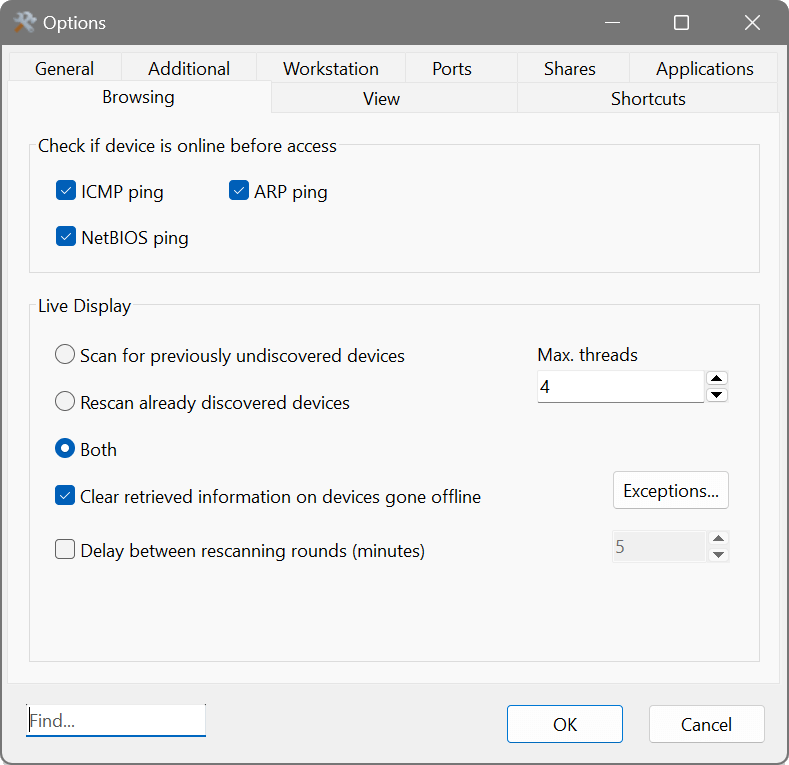
Finally, the Browsing tab enables the Network Scanner to check whether a host is still online when you attempt to explore its folders, or establish a connection to that host. This greatly speeds up some operations, because an attempt to connect an off-line device might temporarily freeze the Network Scanner until the connection fails. You can enable one or more methods to check the availability. Additionally, you can choose a live display mode, whether the Network Scanner must only find previously undiscovered nodes in background, or it must keep rescanning those already discovered, or it must do both. You can also specify the maximum number of threads for background scanning. Don’t forget to turn the live display on in the main menu: View – Enable Live Display.
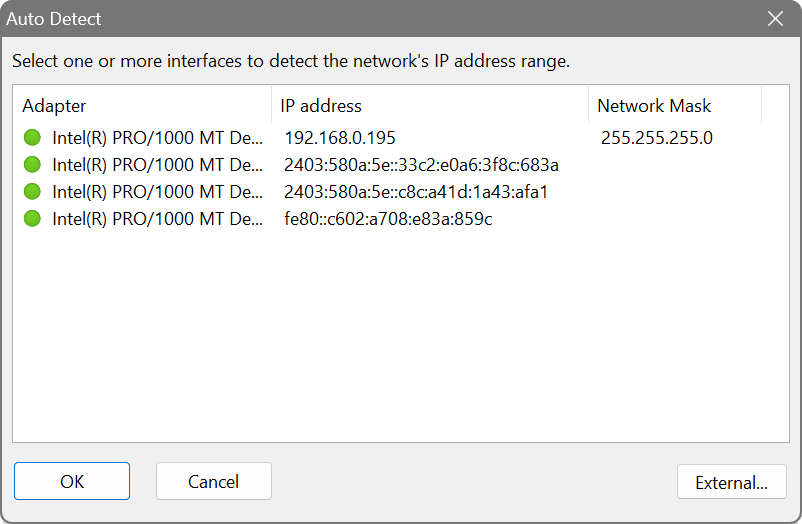
IP address range and automatic detection of network configuration
The SoftPerfect Network Scanner is able to detect your IP range automatically. Select the Options – IP Address – Detect Local IP Range menu item. In the following dialog, select an interface and the program will calculate the IP range of the network. If you are connected to the Internet and are behind a router or proxy server, use the Detect External IP Address command to determine your external IP address (requires Internet connection).

You can add more IP address ranges to scan with the Add button ![]() . Hold Ctrl while clicking this button to add an IPv6 address range rather than IPv4.
. Hold Ctrl while clicking this button to add an IPv6 address range rather than IPv4.
The interpretation of your IP address range depends on the state of the Scan Mode button ![]() . If the button is up, the range is interpreted as a regular one. In this case, the program will sequentially scan all IP addresses within the range. If the button is down, the range is interpreted as a noncontiguous one. In this case, the program will only scan IP addresses whose octets fall in the range. For example, if you specify a range of 10.1.254.1 to 10.9.254.5, the following octets will be scanned:
. If the button is up, the range is interpreted as a regular one. In this case, the program will sequentially scan all IP addresses within the range. If the button is down, the range is interpreted as a noncontiguous one. In this case, the program will only scan IP addresses whose octets fall in the range. For example, if you specify a range of 10.1.254.1 to 10.9.254.5, the following octets will be scanned:
Octet 1: 10
Octet 2: 1 – 9
Octet 3: 254
Octet 4: 1 – 5
Namely, the program will scan:
10.1.254.1, 10.1.254.2, 10.1.254.3, 10.1.254.4, 10.1.254.5
10.2.254.1, 10.2.254.2, 10.2.254.3, 10.2.254.4, 10.2.254.5
10.3.254.1, 10.3.254.2, 10.3.254.3, 10.3.254.4, 10.3.254.5
...
10.9.254.1, 10.9.254.2, 10.9.254.3, 10.9.254.4, 10.9.254.5
This can be useful if you have got a large network and want to scan specific devices in each subnet.
Scanning modes and how the software deals with IPv6
There are three scanning modes supported:
IPv4 address range
In this mode the network scanner simply runs from the lowest to the highest IP address. This the default mode and it can be used by entering an IP address range manually or using the detection feature described above.

IPv6 address range
Likewise, the network scanner runs from the lowest to the highest IP address. Due to a very large pool of possible addresses only up to four last octets can vary. In practice, probably only the last two, for example 2001:db8::1 to 2001:db8::ffff. This can be useful when the IP addresses are allocated by a DHCP server within a known range. This mode can be used by entering an IP address range manually.

IPv6 neighbour discovery
The network scanner sends out a multicast ping to ff02::1 and awaits replies. After that it runs through a list of addresses that responded. This may be handy for discovering auto-configured IPv6 devices. This mode can be used by selecting one of the local addresses in the detection dialog described above.
Scanning
To begin scanning click the Start Scanning button.
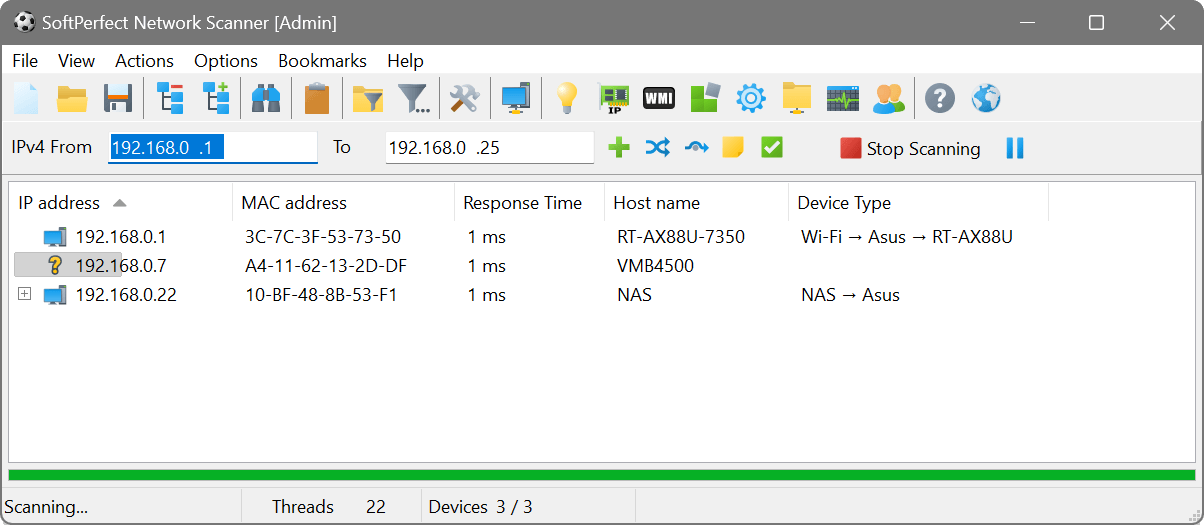
Scan results
When scanning has finished, you will be able to browse the results, save them to a file, map a network drive, explore folders, etc.
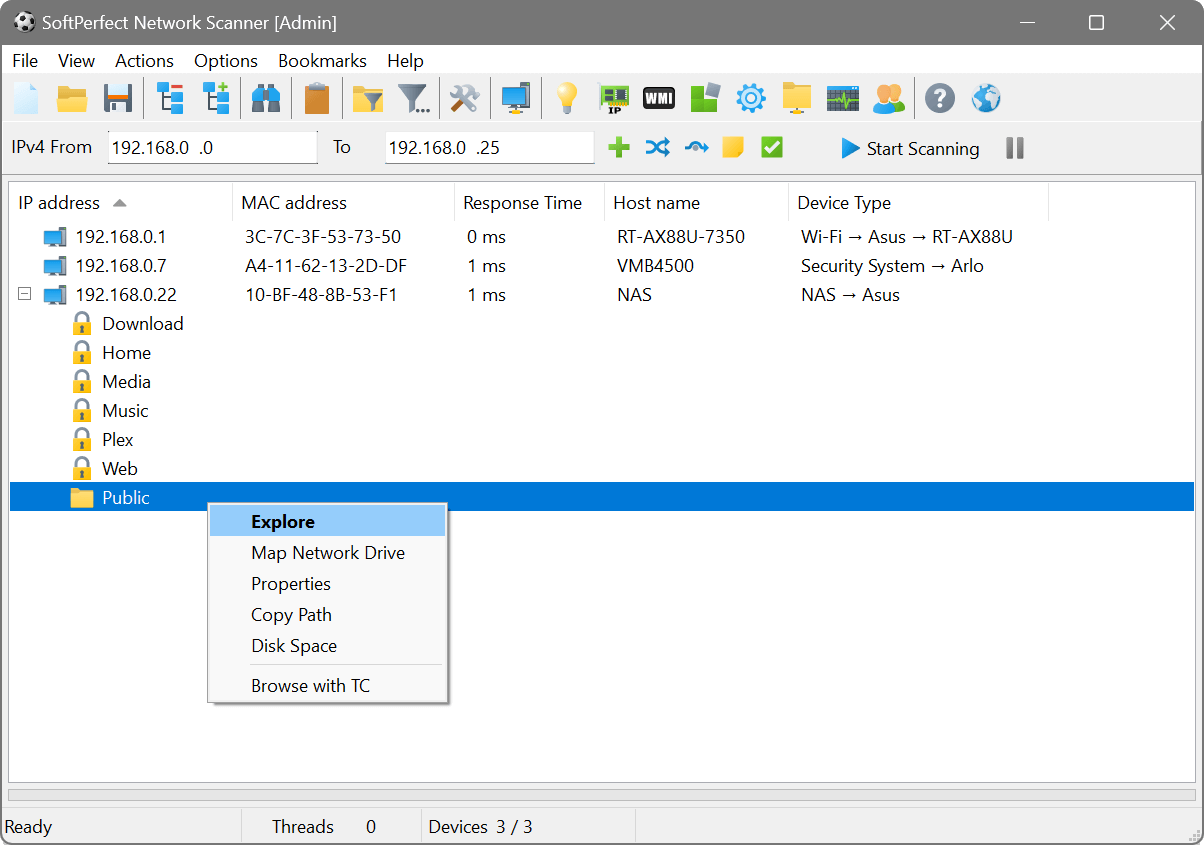
Live display
If you enable the Live Display option (choose View – Live Display from the main menu), the Network Scanner will constantly update scan results to reveal the latest changes in the network. If a host joins or leaves the network, it will be reflected in the main window. The live display log keeps track of devices joining and leaving the network. When the live display is active, choose View – Show Live Display Log from the main menu to access it.
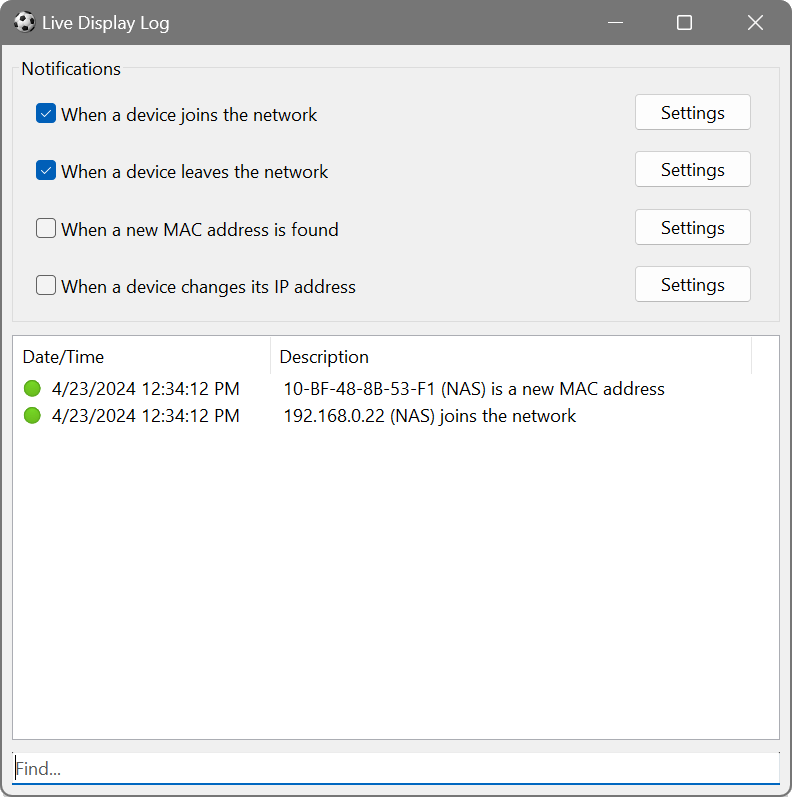
You can specify what happens when a device joins or leaves the network. If any of the When ... options is ticked, a balloon will popup in the notification area. In addition, you can choose one or more actions in the settings: play a sound, launch another application or save the event to a file. It is possible to pass the contents of any column to the application by specifying it in the square brackets as shown below. There is also a pseudo column [event] that you can refer to. It contains the event type, i.e. JOIN, LEAVE, NEWMAC or IPCHANGE.
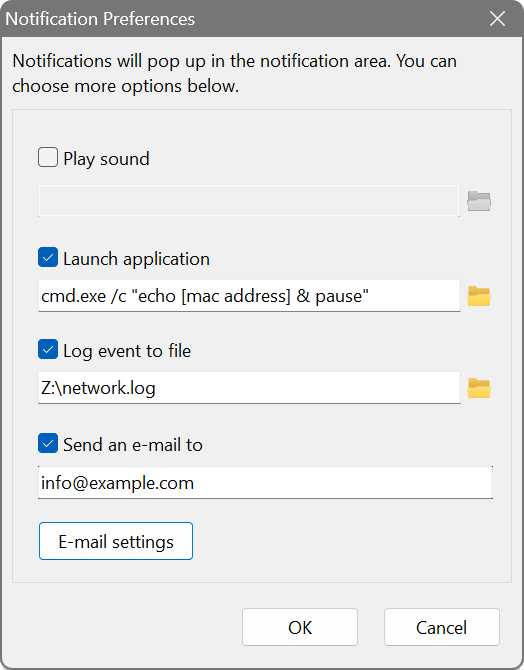
Rogue DHCP server detection
There is a built-in tool searching for active DHCP servers in a LAN segment. It does not require a scan as such. Instead it broadcasts a DHCP discovery message and collects replies from all available DHCP servers. These may be either normal DHCP servers, or rogue servers that are not under administrative control of the network staff. The latter may disrupt connectivity or may be used for network attacks.
To see all active DHCP servers, choose Actions – DHCP Server Discovery from the main menu. In a few moments, you will see a list of all the servers along with offered DNS and gateway addresses.
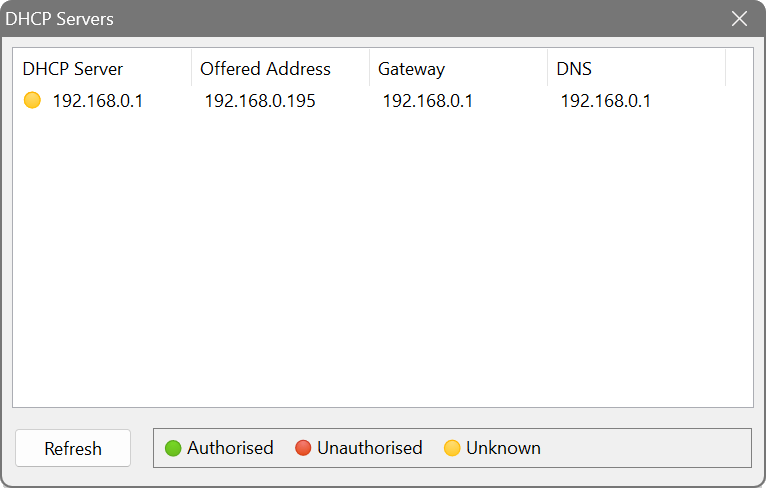
UPnP device detection
Furthermore, the application can discover Universal Plug and Play (UPnP) devices in your network such as media servers, routers and printers. Similarly to the DHCP discovery, it broadcasts a UPnP discovery message and collects replies from compatible devices. To see your UPnP devices, choose Actions – UPnP Device Discovery from the main menu. Click a Device User Interface URL to access the device.
Wake-on-LAN and remote shutdown
To send a “magic” wake up packet to a remote device (its MAC address must be known), choose Actions – Wake-On-LAN from the main menu. To shutdown or reboot a remote PC, choose Actions – Remote Shutdown. You can also suspend or hibernate a remote computer by choosing Actions – Remote Suspend/Hibernate.
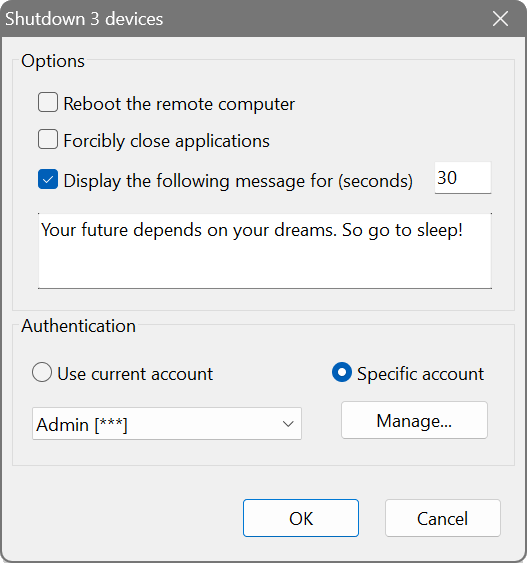
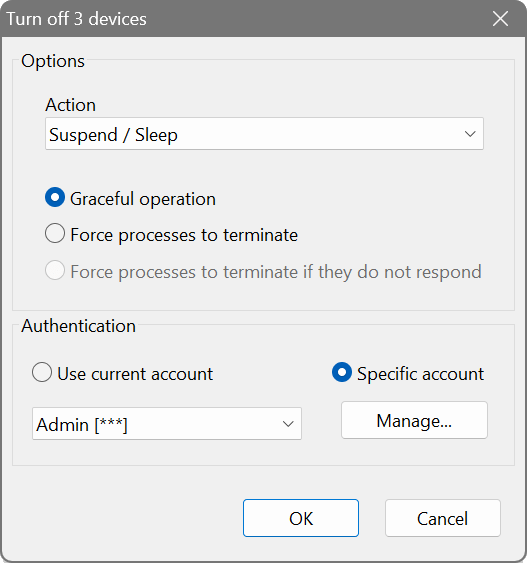
To shutdown or suspend a remote computer, several criteria must be met:
- Administrative shares are enabled.
- Administrator has got a non-empty password.
- Simple file sharing is turned off.
- Administrative shares IPC$ and ADMIN$ are accessible.
Otherwise you may encounter either the Access is denied or the Network path not found error.
WMI Query builder and scanning
The Network Scanner is capable of running WMI (Windows Management Instrumentation) queries against the hosts being scanned. To create a WMI query, choose Options – WMI from the main menu. Queries are written in a special language called WQL, similar to SQL.
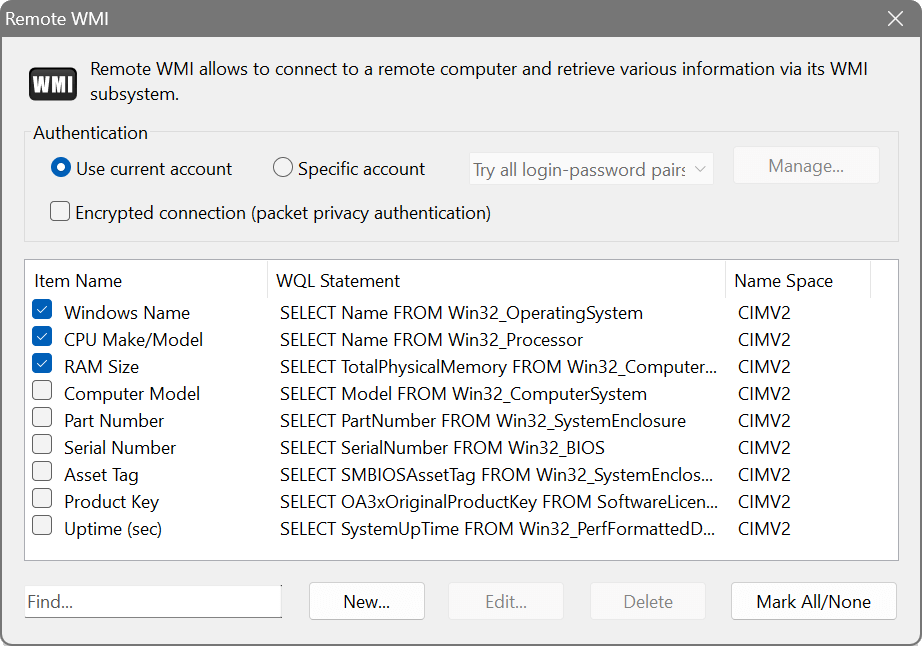
The New button allows you to easily construct simple WQL queries. It merely connects to your computer’s WMI subsystem and lets you pick a WMI class and parameter to be used in the query. When you have one or more WMI queries enabled, there will be additional columns shown in the scan results.
Remote file, registry and services
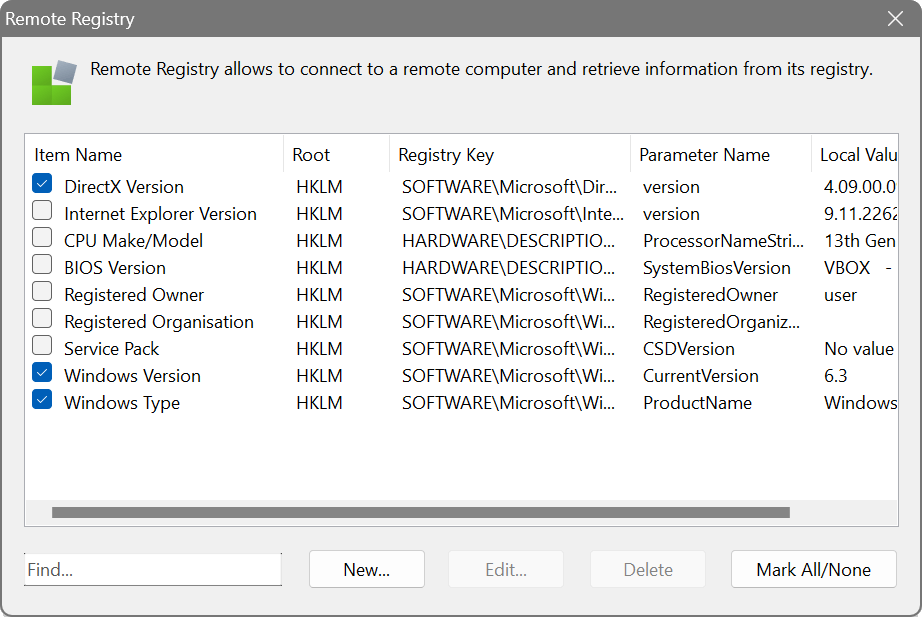
Firstly, the application can connect to the remote registry of remote PCs running Windows, provided the remote registry service is started. Secondly, it can also connect to their file system via administrative shares (C$, D$, E$, etc) and retrieve information about a specific file. Thirdly, it can connect to the remote service manager and query the status of one or more services. These features are useful mainly for network administrators maintaining large networks and can be accessed by choosing Options – Remote Registry, Options – Remote File or Options – Remote Services from the main menu.
There are several predefined entries in the list, and you can easily add new items to retrieve data about hardware and software specific to your environment. The columns are as follows: Item Name is a name of the entry, Root represents one of the root registry hives, Registry key contains the path to the value of interest, Parameter Name is the value name to be retrieved, and Local Value shows the value in the local registry on your computer.
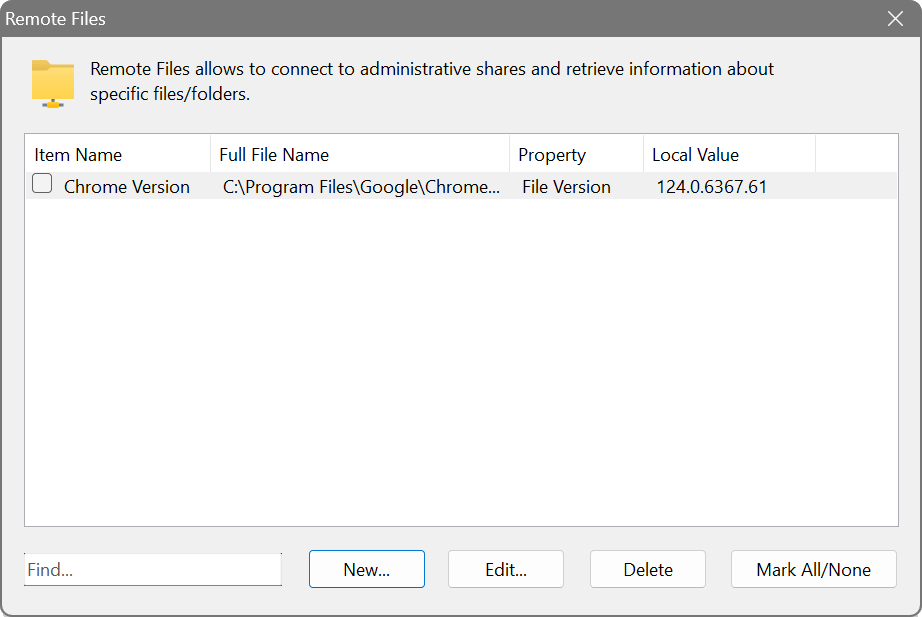
Likewise, provided the administrative shares are enabled and accessible, you can pull out information about a specific file or folder on remote computers. For example, you want to find out the version of an application, or when a log file changed, or how large a particular file is. To do so, enter the full name of a file and choose the property you want to retrieve.
On the following screenshot, the application is configured to access the Chrome executable and display its version. Drive letters are substituted with the relevant administrative shared folders. For example, if you scan the range from 10.0.0.1 to 10.0.0.10 with these settings, the application will attempt to display the version information embedded in the files \\10.0.0.1\C$\Program Files (x86)\Google\Chrome\Application\chrome.exe, \\10.0.0.2\C$\Program Files (x86)\Google\Chrome\Application\chrome.exe, etc.
It also possible to use wildcards, for example C:\Program Files (x86)\Google\Chrome\Application\*.exe will process all executable files in C:\Program Files (x86)\Google\Chrome\Application.
Furthermore, you can have variable parts in path names, which is especially useful in a multilingual environment. If you have a few possible locations for your file, list them in brackets, separated by a vertical bar, as in the following example: C:\[Program Files|Program Files (x86)|Programme]\Google\Chrome\Application\chrome.exe. In this case, the Network Scanner will try three different paths listed below and proceed with the first valid one.
- C:\Program Files\Google\Chrome\Application\chrome.exe
- C:\Program Files (x86)\Google\Chrome\Application\chrome.exe
- C:\Programme\Google\Chrome\Application\chrome.exe
Lastly, you can retrieve information about the status and configuration of a service on remote computers. For example, if you want to make sure that the wuauserv service is up and running, turn the pre-defined item on, as shown below. The Network Scanner will then connect to each computer’s service manager and query that information.
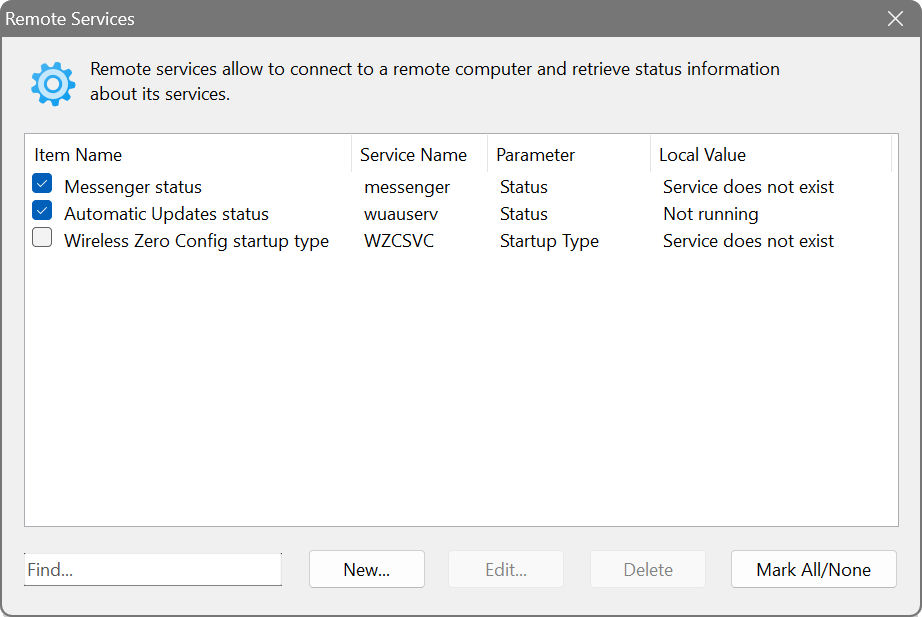
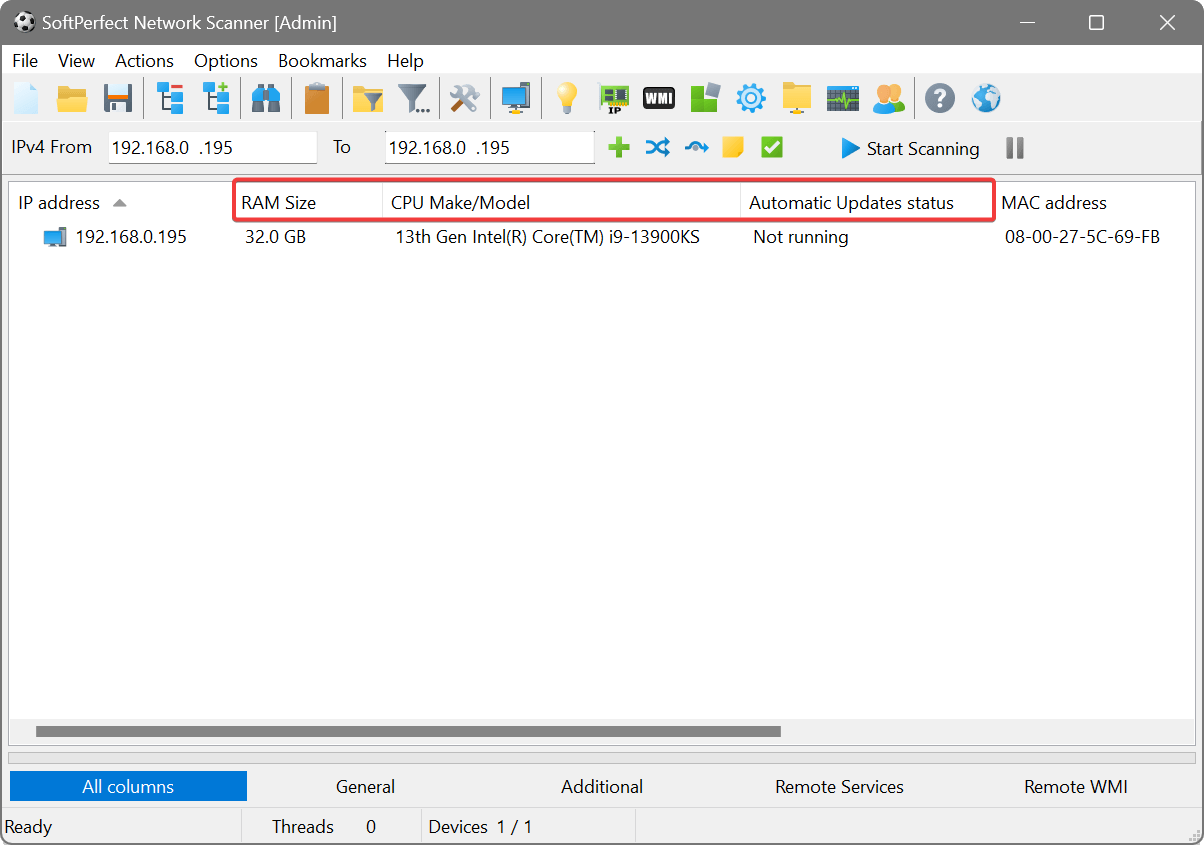
There will be additional columns showing the retrieved information:
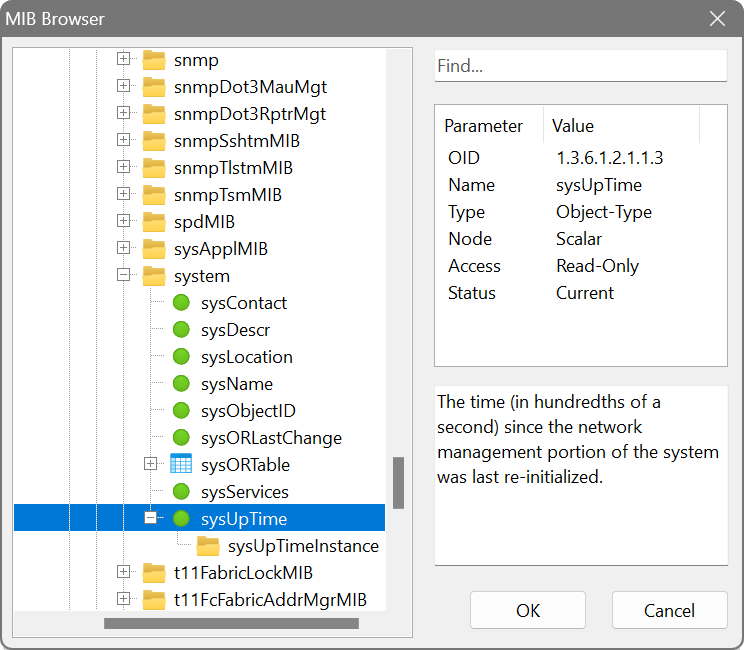
Remote SNMP query
Network Scanner can look for machines that have an SNMP service running. You can specify a community (e.g. public or private) and a MIB OID number. The application automatically determines the type of data received and displays it in a readable form.
All three versions of SNMP are supported. A default Windows SNMP implementation is used if you choose Windows built-in or you can use a specific SNMP version.
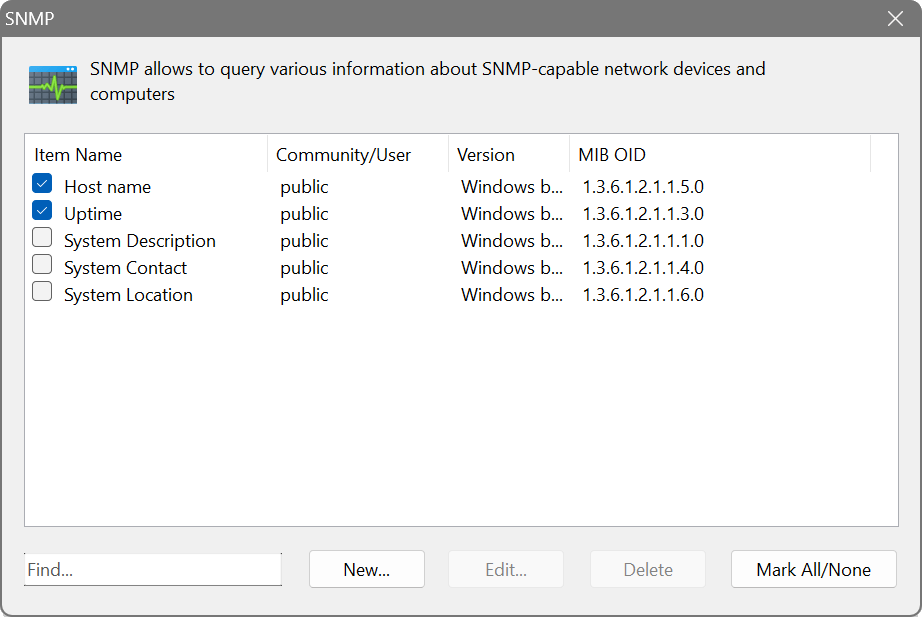
There is a built-in MIB browser for easy selection of OIDs. You can add your specific MIB files to %APPDATA%\SoftPerfect Network Scanner\Mibs.
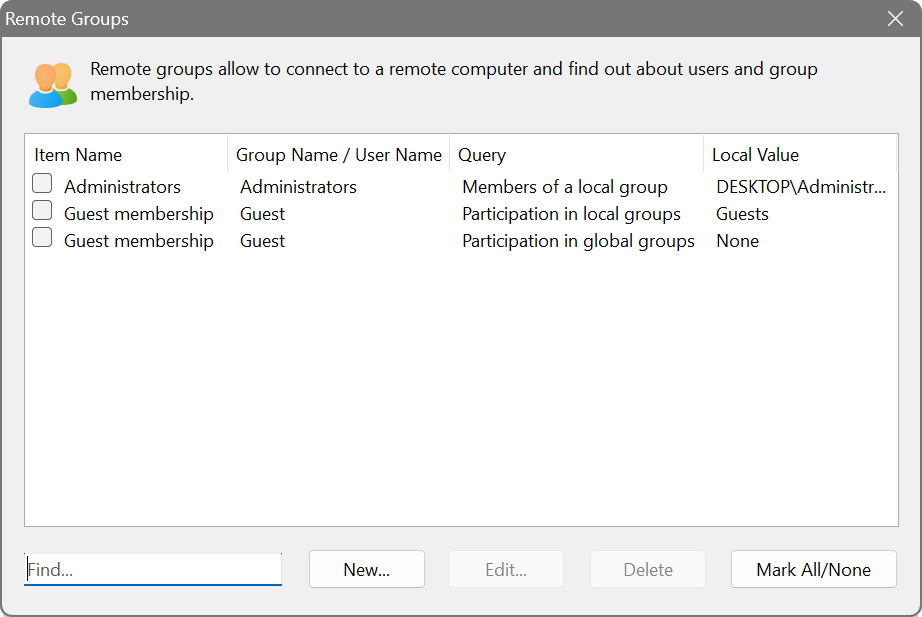
Remote groups query
If you need to find out what users participate in a particular group, or what groups a user belongs to, you can use this feature. The Network Scanner connects to each computer and retrieves local or global group membership:
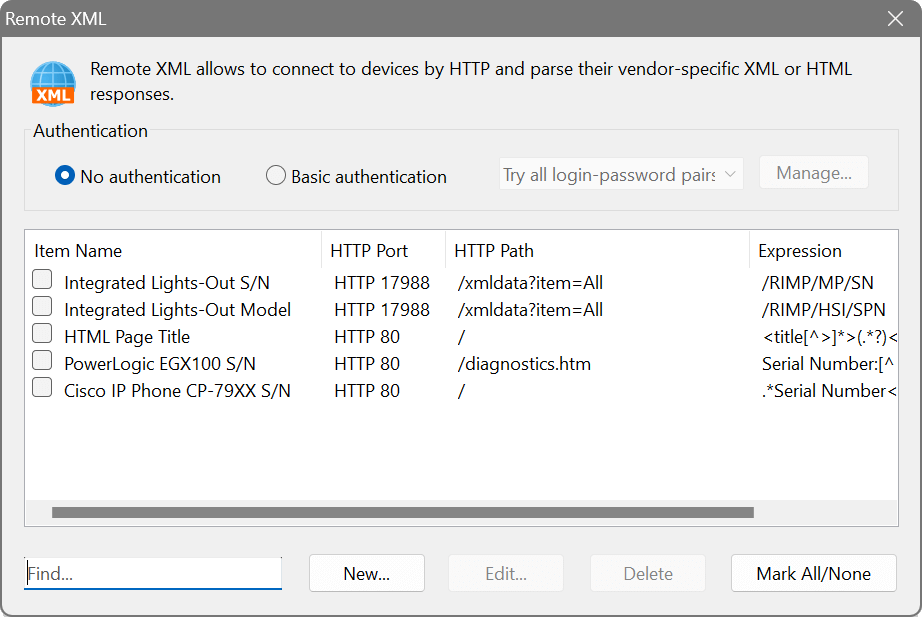
Remote XML
There is an advanced feature to obtain device configuration and status. It allows you to send a HTTP request and parse a XML, HTML or text response. It works virtually for any device that has got a built-in web-server producing text output, which can then be parsed with XPath or a regular expression. For example, there is a couple of default entries to retrieve HP Integrated Lights-Out properties:
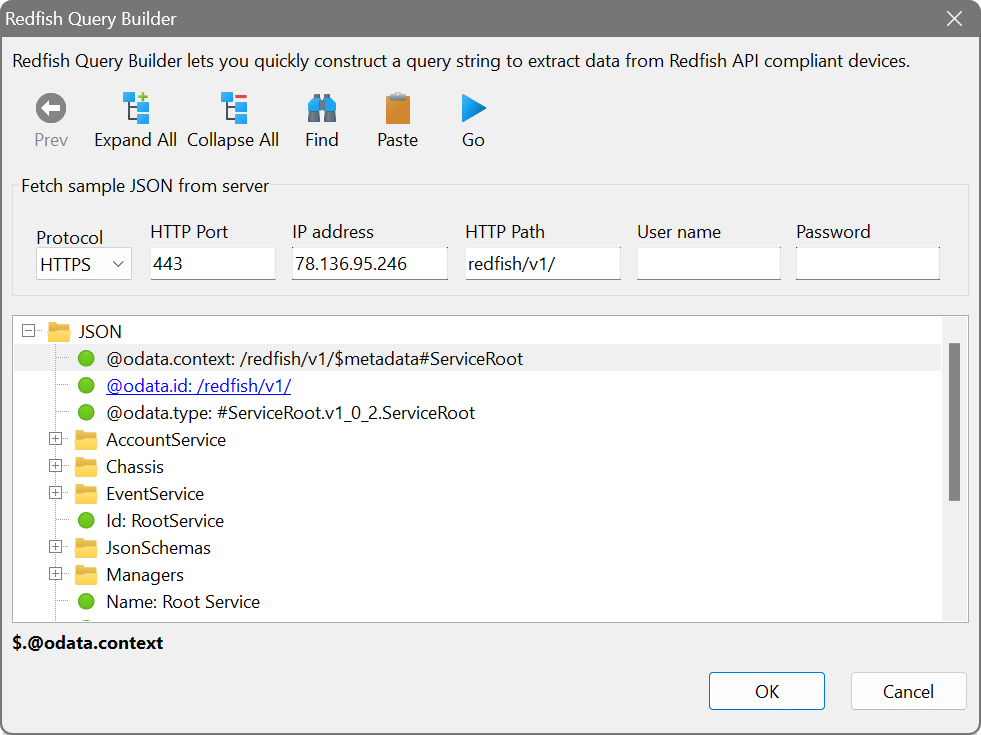
Remote JSON
Just like the Remote XML feature, it allows you to extract data from a JSON response received over HTTP. Remote JSON includes a query builder for quickly choosing what data to extract from a JSON tree.
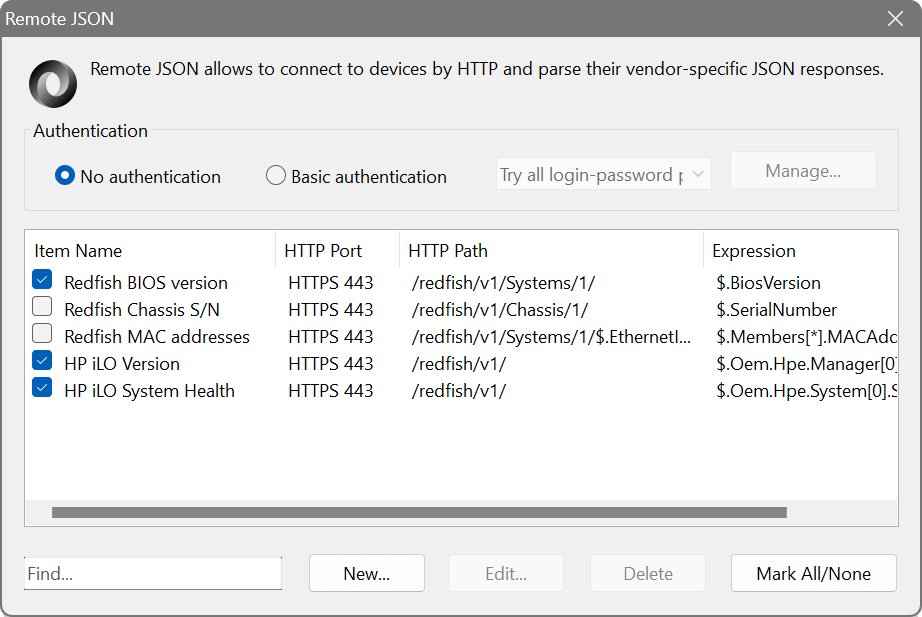
In addition to regular JSON, the application supports the Redfish Scalable Platforms Management API. The Redfish API is implemented in a wide range of servers, from stand-alone servers to rack mount and bladed environments, and allows you to manage those systems.
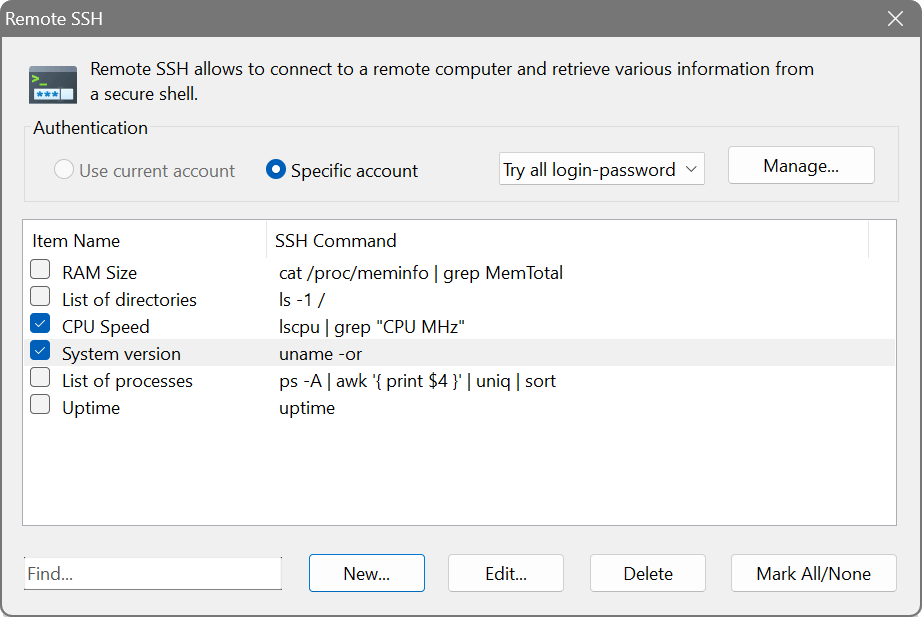
Remote SSH
If you have Unix/Linux computers, you can use this feature to connect to their shell and execute one or more commands.
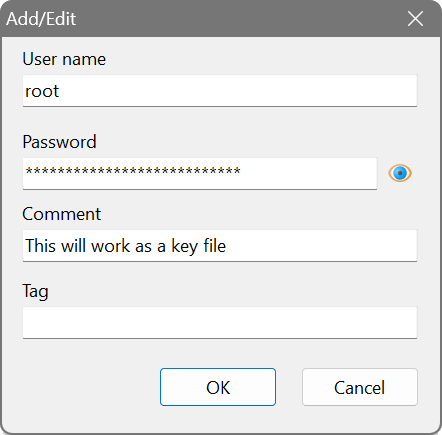
Both the password-based and the key-based authentication types are supported. To use a key instead of a password, specify a full path to the key file as shown below:
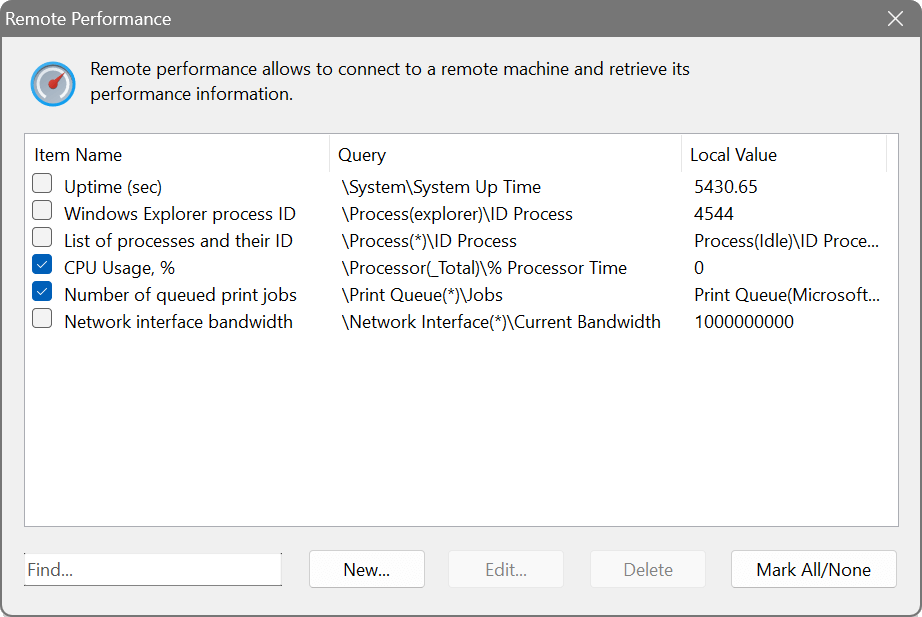
Remote performance
This feature makes use of the Windows Performance Counters to obtain various live system data such as CPU usage or information about processes. It needs the Remote Registry service to be running and accessible.
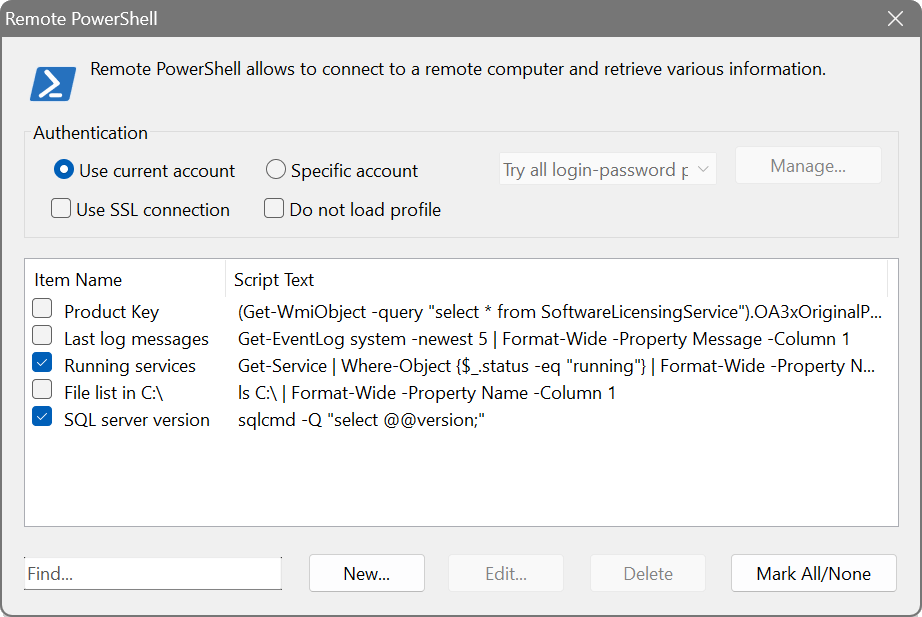
Remote PowerShell
The software can execute your PowerShell scripts against remote computers. It works by executing the following command in a PowerShell console and capturing its output:
Remote Scripting
The software can execute a custom VBScript or JScript against remote computers. It uses the Windows Script Host and most existing scripts would work, only requiring to replace WScript.Echo with Output.Write and obtain current IP address from Input.Current
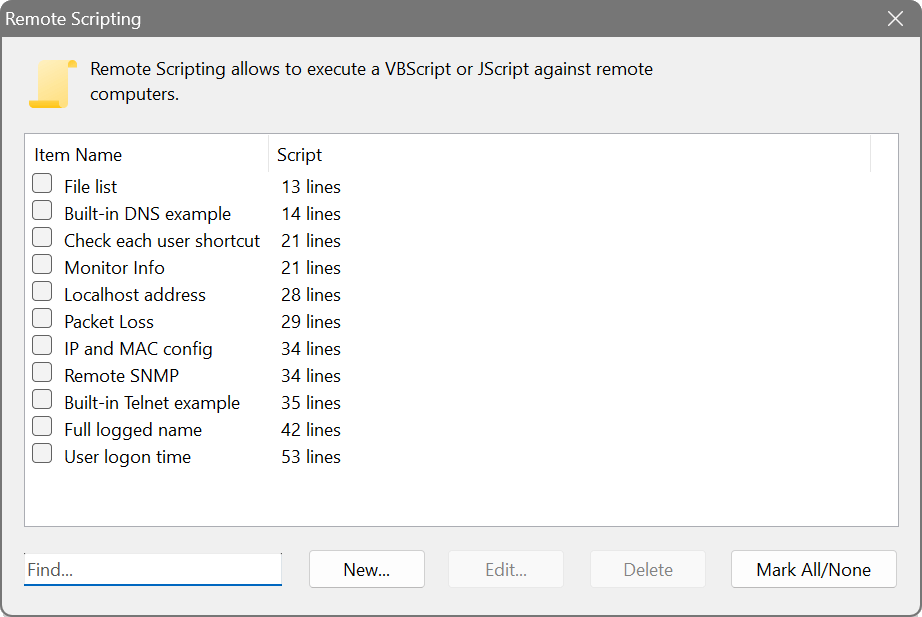
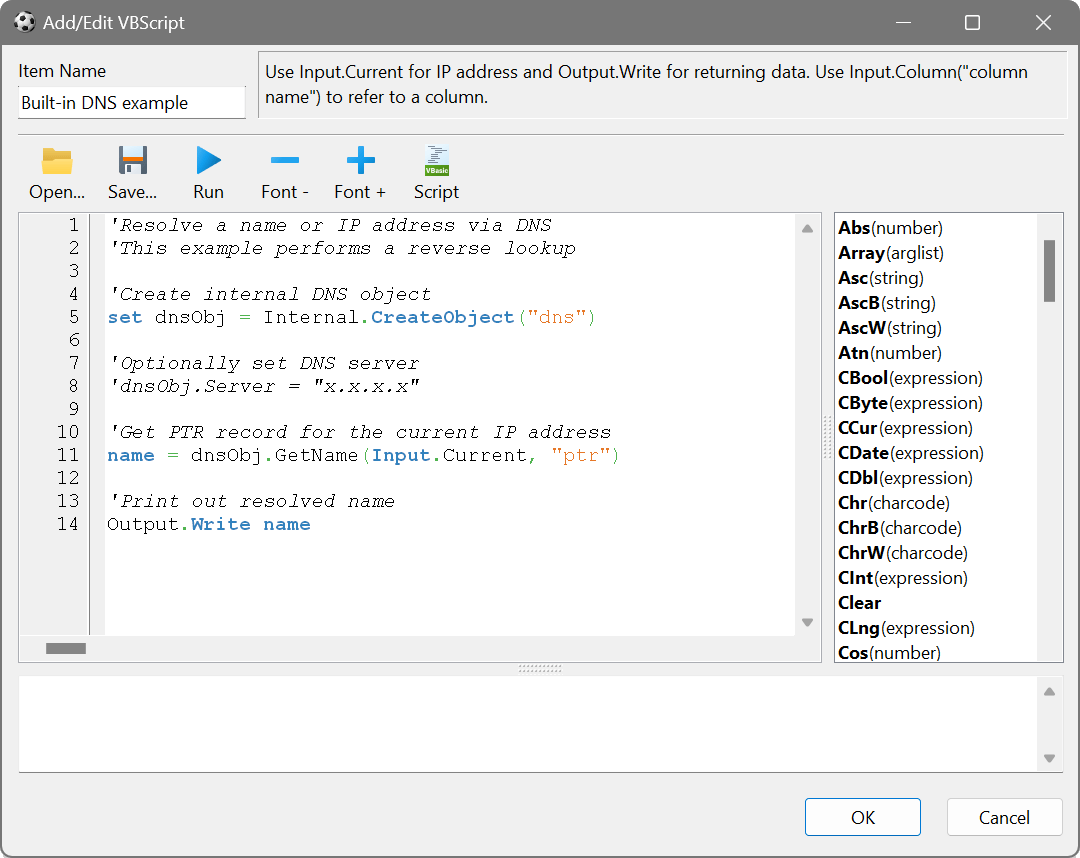
In addition to regular automation objects that can be created with CreateObject(), you can call Internal.CreateObject() to create and use the following built-in objects:
Telnet
| Method | Description |
|---|---|
| Connect | Establishes a connection to the configured Host and Port. |
| Disconnect | Terminates a connection established with the above call. |
| Send("string") | Sends a string to the remote host. For sending a command you may need to add vbCrLf. |
| WaitFor("string") | Waits for a string to be sent by the remote host. Useful for detecting prompts and sending data after that. |
| string Recv("terminator") | Reads data up to the specified terminator. To read to the end of line use vbCrLf as the terminator. |
| Property | Description |
| Host | Host name or IP address to connect to. |
| Port | Port number to connect to. The default port is 23. |
Process
| Method | Description |
|---|---|
| Execute("command-line-string") | Launches the specified console program and waits for its completion. |
| Property | Description |
| ExitCode | A numeric exit code with which the program terminates. |
| Output | A collection of strings containing captured console output. |
DNS
| Method | Description |
|---|---|
| GetName("target","type") | Sends a DNS request to the DNS server specified in the Server property. The first parameter is a host name or IP address to be resolved. The second parameter is the record type, usually "a" or "aaaa" for a regular name lookup or "ptr" for a reverse lookup. |
| Property | Description |
| Server | One or more comma-separated DNS server addresses. If not specified, the default servers will be used. |
SNMP
| Method | Description |
|---|---|
| SendRequest | Sends an SNMP request to the device specified in the Host property. Request parameters are set in the Query property. If this method succeeds, the response is available in the Reply property. |
| Property | Description |
| Host | Target host name or IP address. |
| Query | The Query object defines request parameters. |
| Reply | The Reply object contains response details. |
| Query Object | Description |
| Query.AddOid("string") | Adds an OID string to the request. Multiple OIDs can be added. |
| Query.SetOid("string") | Sets an OID string for use in the request. Any previously added OIDs are deleted. Pass an empty string to clear all added OIDs. |
| Query.Version | SNMP version number to use: 1, 2 or 3. |
| Query.PduType | PDU type used in the request: &hA0 (GetRequest), &hA1 (GetNextRequest) or &hA5 (GetBulkRequest). |
| Query.Community | Community string for use in SNMPv1 and SNMPv2. |
| Query.V3Security | SNMPv3 security mode string: NoAuthNoPriv, AuthNoPriv or AuthPriv. |
| Query.V3AuthMode | SNMPv3 authentication algorithm string: MD5 or SHA1. |
| Query.V3PrivMode | SNMPv3 privacy algorithm string: DES, 3DES or AES. |
| Query.V3UserName | SVMPv3 user name string. |
| Query.V3AuthPass | SVMPv3 authentication password string. |
| Query.V3PrivPass | SNMPv3 privacy password string. |
| Query.MaxRepetitions | Target max-repetitions value for a bulk request. |
| Query.NonRepeaters | Target non-repeaters value for a bulk request. |
| Reply Object | Description |
| Reply.ErrorStatus | A numeric SNMP error code. |
| Reply.Items | Collection of reply items. |
| Reply.Items.Count | Number of items in the collection. |
| Reply.Items(index).Oid | A string value containing response OID. |
| Reply.Items(index).Value | A string value containing response data. |
| Reply.Items(index).Type | A numeric value containing response data type. |
Integration with Nmap
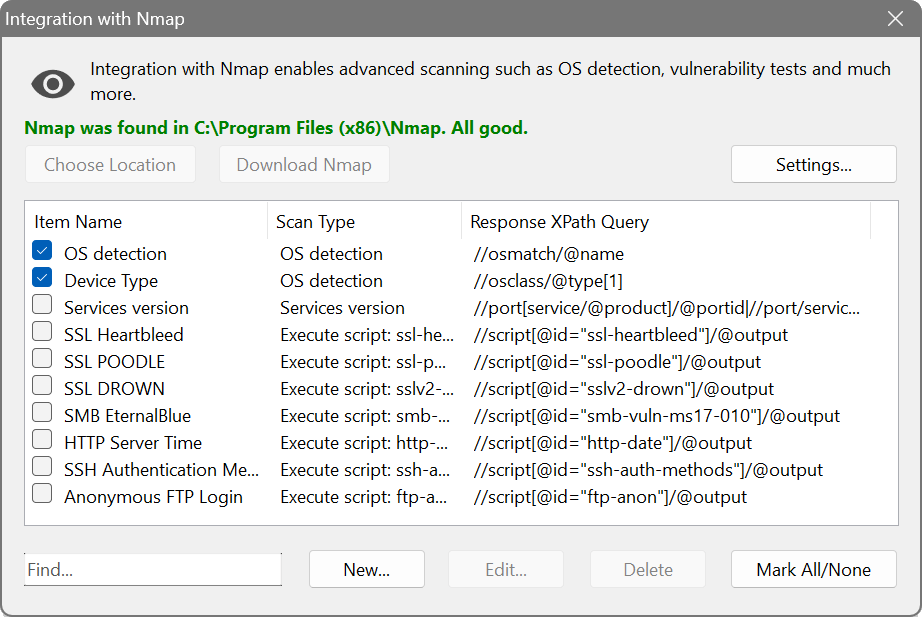
There is integrated support of Nmap, a free console-based tool that lets you detect OS name, device type, service versions, and much more. It comes with a collection of scripts for advanced discovery, vulnerability testing and malware detection.
Since Nmap is a console tool, it is executed with a set of parameters according to your chosen options. Upon termination, its XML output is captured and parsed with an XPath expression. After that, the extracted data is available in the Network Scanner’s user interface.
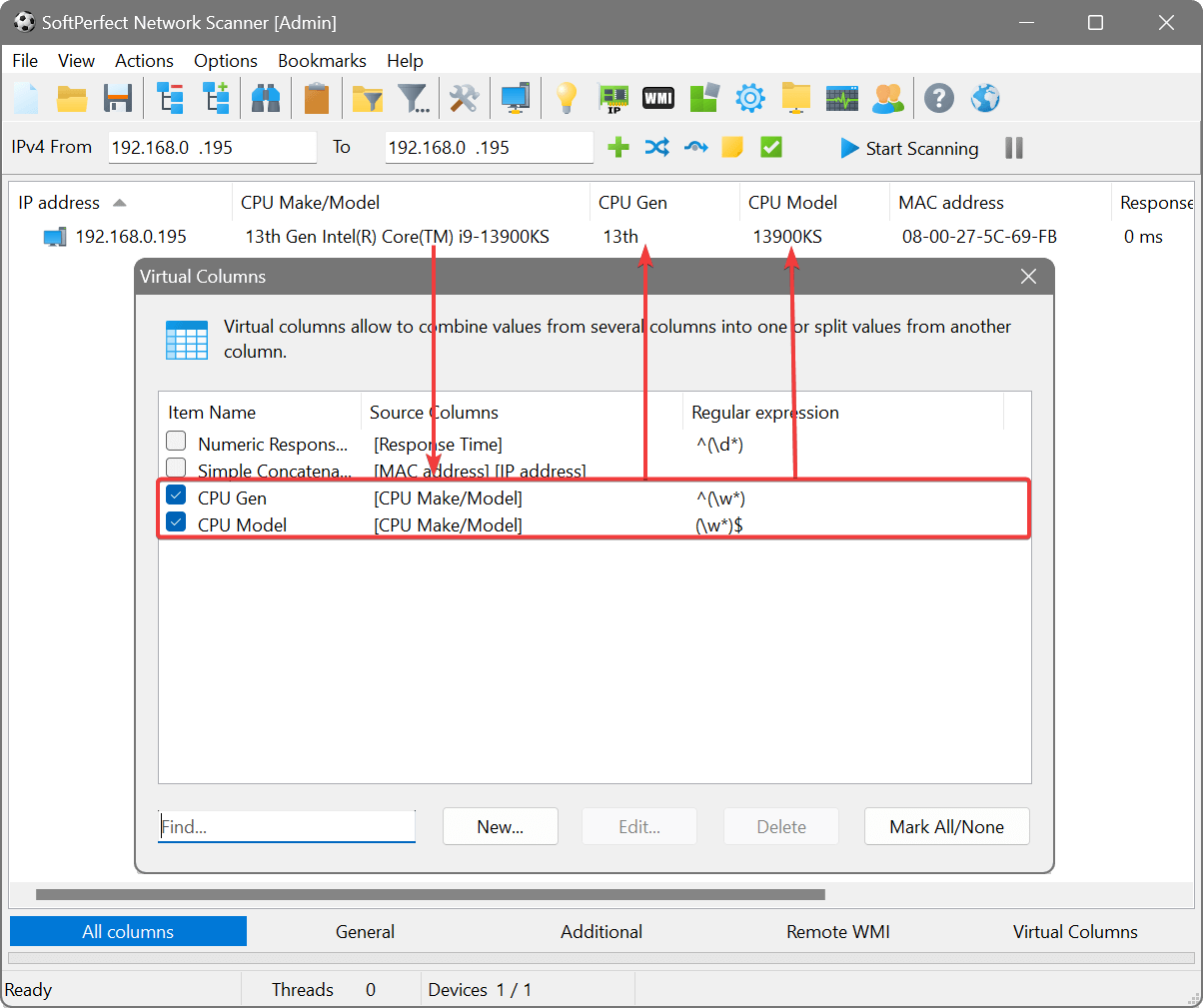
Virtual Columns
Sometimes you may want to break down several pieces of information returned in a single column into independent columns. This can be easily done via Options – Virtual Columns.
These columns do not retrieve any information from remote devices. Instead, a virtual column takes a value from one or more real columns and optionally applies a regular expression to it.
In this example we retrieve CPU Make/Model and then break it down to CPU Gen and CPU Model:
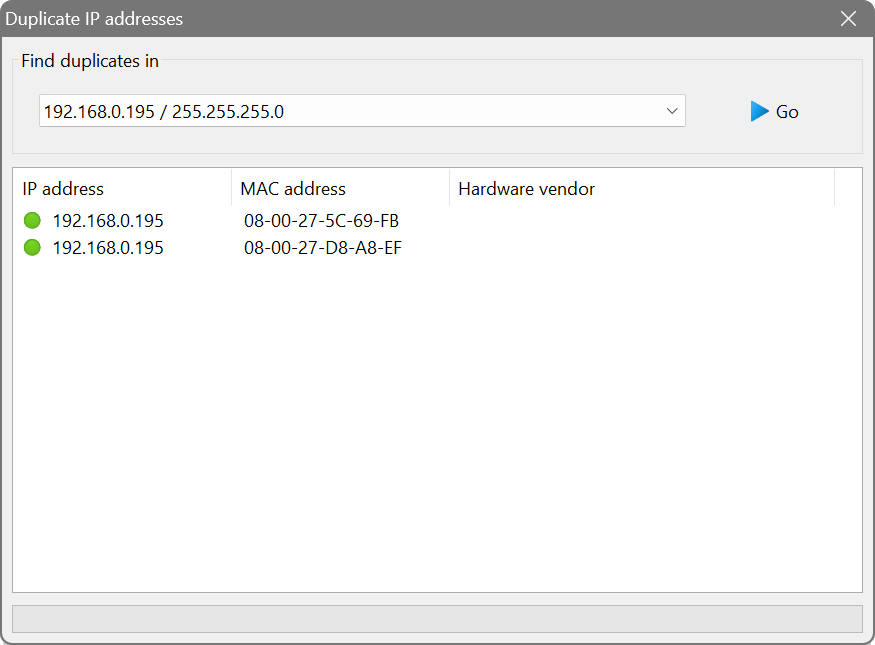
Duplicate IP address detection
Occasionally, two or more devices in a network can be assigned the same IP address, which disrupts connectivity between these devices. Use this feature to discover any duplicate IP addresses in the current subnet.
The detection works by sending an ARP request to every address and collecting ARP replies. If two or more devices respond to one request, this means they have been erroneously assigned the same address and this situation needs to be resolved.
You may need to download and install Npcap to use this feature, as it requires low-level access to the network card.
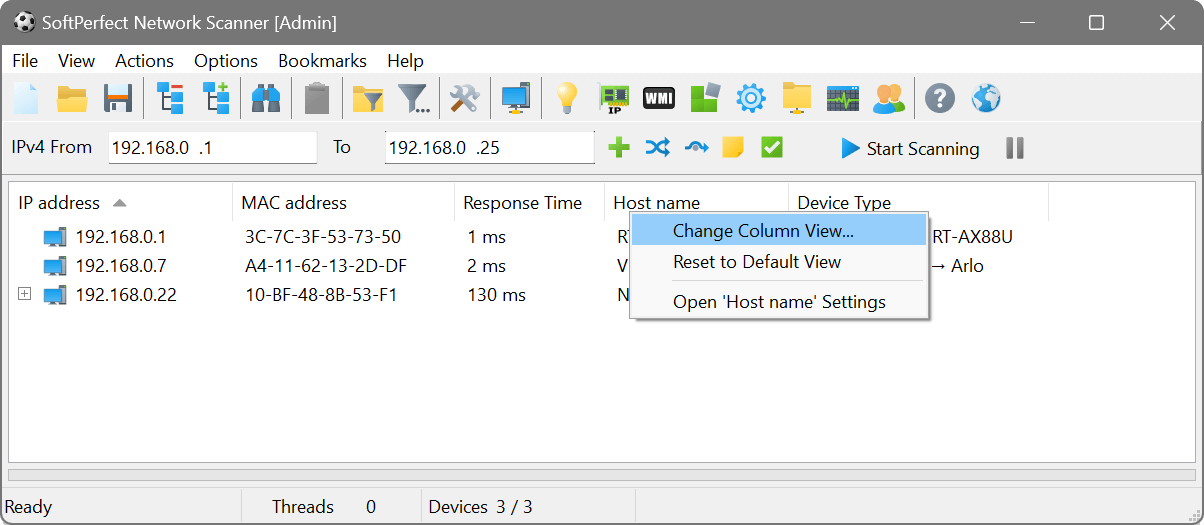
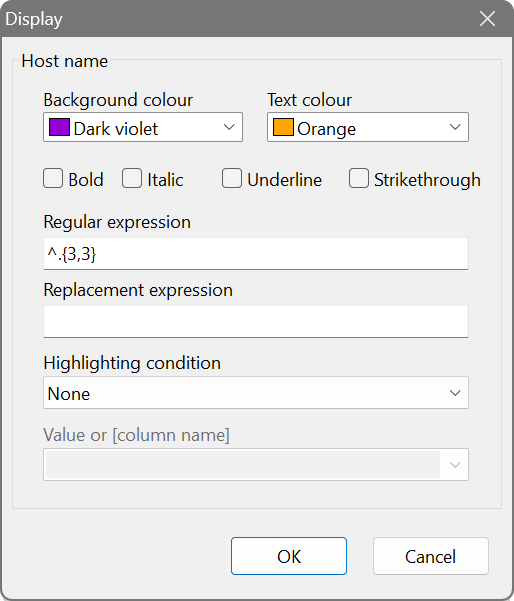
Output presentation
You can change any column’s background colour and text colour for easy identification and highlight certain values:
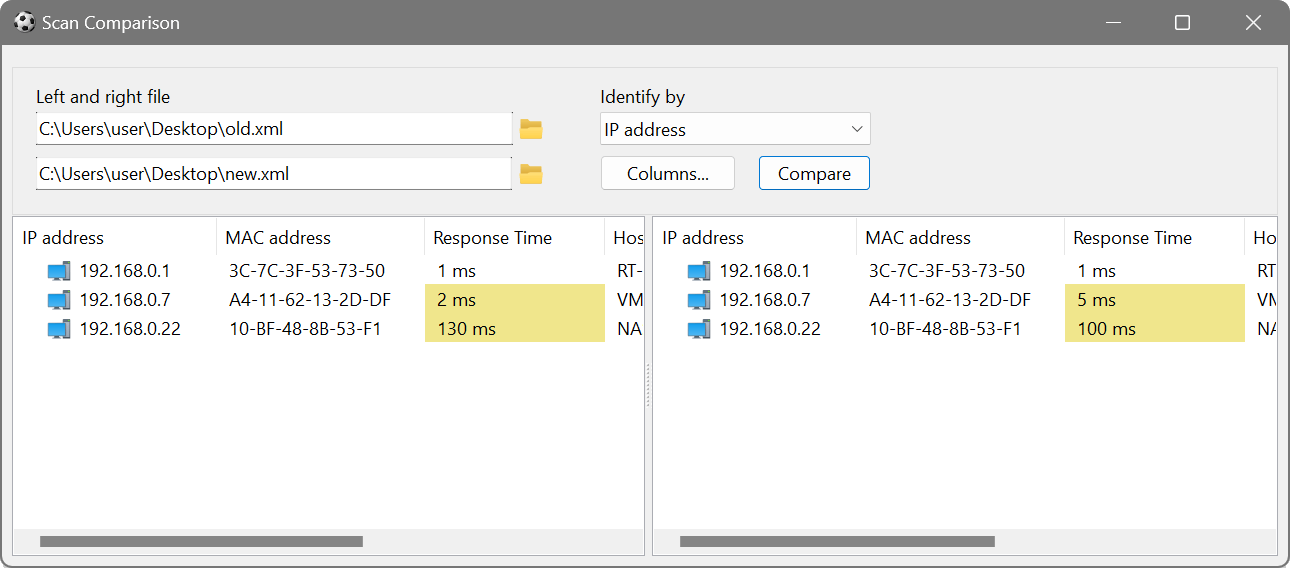
Scan Comparison
You can compare the differences between any two scans by choosing File – Compare Scans and loading the XML files.
Tips and tricks
- Many scan items can be quickly accessed without going to a specific scan and searching for the entry. Try right-clicking a column heading and choose Edit <Item Name>.
- When clicking a bookmark in the Network Scanner’s main menu, the current IP addresses will be replaced with those assigned to the selected bookmark. Hold the Ctrl key to append them instead. The same applies to choosing one or more IP addresses in the automatic IP address detection dialog and Importing IP/Hostnames.
- It is possible to group bookmarks or custom applications that you define within the Network Scanner. Specify a vertical bar to create groups of items. For example, try naming your bookmarks as Network A | Subnet 1, Network A | Subnet 2 or naming your applications as FTP clients | FileZilla, FTP clients | Total Commander.
- If it appears that all IP addresses are detected as active, set the Ping Method to ICMP only. This is happening because when you are scanning a different subnet, the default gateway may respond to every ARP request with its own MAC address rather than the target device’s address, thus misleading the Network Scanner.
- If you want to send Wake-On-LAN packets to a subnet specific broadcast address, change the default broadcast address to 0.0.0.255. In this case, when you are adding a device to wake up from the main view, the actual device’s IP addresses will be combined with the default address. For example, when adding 192.168.1.10 and the default broadcast address being 0.0.0.255, a new WOL entry will have 192.168.1.255.
- In Remote SNMP discovery OIDs may contain variable parts with 0% and %1. The former will be replaced with the octets of a scanned IP address. The latter will be replaced with the octets of a scanned MAC address. For example, the OID of 1.3.6.1.2.1.4.20.1.3.%0 can be used to extract a device’s network mask.
Command line switches
You can use the following switches as netscan.exe /switch1 /switch2 ... switchN.
/auto:filename.[txt|htm|xml|csv|json|db] runs scan with global settings and exports the results to a file, i.e. /auto:"c:\desktop\result.txt". Specify a corresponding extension to produce a file of that type. For example:
netscan.exe /hide /auto:"c:\desktop\result.txt"
netscan.exe /hide /auto:"c:\desktop\result.htm"
netscan.exe /hide /auto:"c:\desktop\result.csv"
To run a scan automatically without exporting to a file, specify /auto without a parameter. It is also possible to have the current date and time in the file name. Use any combination of the following tokens, each enclosed between two percent signs: y, yy, yyyy, m, mm, mmm, mmmm, d, dd, ddd, dddd, h, hh, n, nn, s, ss. For example, date_%yyyy%%mm%%dd%_time_%hh%%nn%.csv.
/live:filename.[txt|htm|xml|csv|db] is similar to the above switch. Unlike the /auto switch, the /live switch leaves the Network Scanner on and enables the live display. The specified file is updated after every complete round of the live scan, so the file always reflects latest changes.
/config:filename.xml loads the specified XML configuration file in the application.
/hide hides the main window (silent mode). If the network scanner was launched from a command prompt, it would output its progress in the command prompt window. Note that because the network scanner isn’t a true console application, the command processor and the application’s output may sometimes overlap. For better readability, use the following command to launch the application:
start /wait netscan.exe /hide ...
/load:filename.xml loads the specified XML result set in the application. It is possible to rescan it with the /auto switch.
/cols:col1;col2;col3 applies to the /auto command and exports only the specified columns to a file. Otherwise all visible columns are exported. Example: /cols:"Host Name;MAC Address".
/range:from-to Sets an IP address range for scanning, for example: /range:192.168.0.1-192.168.10.254. Multiple ranges should be comma-separated. To pass a noncontiguous IP address range, append #N, for example /range:10.64.1.1-10.64.5.10#N.
/range:type Automatically detects the current IP address range for scanning. Valid types are all, v4 and v6. For example, /range:v4 will detect all available IPv4 ranges.
/append applies to the /auto command for text and CSV files. Appends the results to a file rather than overwrites it.
/merge applies to the /auto command for text and CSV files. Merges the results with those in a file, output lines are sorted and duplicates are removed.
/splitmv applies to the /auto command for text and CSV files. Splits cells that contain multiple comma-separated values into separate rows.
/wol:mac sends a Wake-On-LAN magic packet to the specified MAC address and immediately exits. Example: /wol:AABBCCDDEEFF.
/wolfile:filename.txt allows you to specify a text file with MAC addresses to wake-up, e.g. /wolfile:c:\myfile.txt where the file is a plain text file containing one MAC address per line.
/wakeall sends a WOL packet to all devices configured in the WOL manager and immediately quits.
/file:filename.txt loads the specified text file and feeds in IP addresses to be scanned. Use this switch with /auto or /live. There must be one address or range per line in one of the following notations. Any mismatching lines in the file will be discarded. Another way to import a file is to choose File – Import IP/Host Name List from the main menu.
| Line | Example | Interpretation |
|---|---|---|
| x.x.x.x | 10.0.0.1 | Single IPv4 address |
| x.x.x.x- |
10.0.0.1- |
IPv4 address range |
| x.x.x.x/y | 10.0.0.1/24 | IPv4 address/ |
| x:x:x:x:x:x:x:x | 2001:db8::1 | Single IPv6 address |
| x:x:x:x:x:x:x:x- |
2001:db8::1- |
IPv6 address range |
| x:x:x:x:x:x:x:x/y | 2001:db8::/120 | IPv6 address/ |
| hostname | google.com | Host name (will be resolved to an IP address) |
End User Licence Agreement (EULA)
This software and the included documentation is copyright SoftPerfect Pty Ltd. All rights are reserved. The software may be used, installed or copied only in accordance with the terms of the licence described in the following paragraphs.
DISTRIBUTION TERMS
The evaluation version of the software may be freely distributed, provided that the original distribution package is not modified in any way.
EVALUATION VERSION
This is not free software. You are hereby licensed to use this software for evaluation purposes without charge. The evaluation version may be of a limited duration, or have some features limited or disabled. To use the software without these restrictions, you need to purchase a licence.
GRANT OF LICENCE
The software is licensed, not sold. Upon purchase of a licence, SoftPerfect grants you non-exclusive, non-transferable right to use the software and all its features according to the terms of this EULA and the purchased licence type as described in the Licence Types section.
LICENCE TYPES
- Single Device Licence grants the purchaser, or agents of the purchaser, rights to install and use the software on one device only (e.g. computer, server, USB flash drive or virtual machine) at any given time. The licence can be reinstalled on the same device at any time, or deleted from one device and then moved to another. To install and use the software on more than one device simultaneously, you must purchase the corresponding number of single device licences or one of the special licences listed below.
- Multiple Licence Pack grants the purchaser, or agents of the purchaser, rights to simultaneously install and use the software on up to as many devices as is stipulated by the quantity in the pack. For example, the “Up to 10 Devices” pack allows installing and using the software on up to ten devices at the same time. Each device licence within the pack is identical to a single device licence.
- Site Licence grants an organisation, or agents of an organisation, rights to install and use the software on an unlimited number of devices within one organisation site, including any cloud-based installation and use performed from that site. An organisation site is defined as a location, or group of locations, used by the organisation that are all within 100 miles (160 kilometres) of each other.
- Worldwide Licence grants an organisation, or agents of an organisation, rights to install and use the software on an unlimited number of devices at an unlimited number of locations used by the organisation, including any cloud-based installations and use performed from those locations. If not listed, please contact us for the worldwide licence price.
- OEM Licence grants an organisation, or agents of an organisation, rights to use and distribute the software with their own hardware or software products. These products must provide substantial additional functionality to this software, and not include any potentially unwanted programs.
Where applicable, additional licence subtypes include:
- Home Licence grants a private individual rights to install and use the software at home, that is in a place of residence, for domestic purposes with no intention to generate income.
- Business Licence grants an organisation (a company, corporation, firm, enterprise or institution, or part thereof) or a person rights to install and use the software in a commercial and non-commercial environment for the purposes of or in connection with running a business, supplying products or services to other organisations or individuals, or generating income.
DISTRIBUTION OF LICENCE KEYS
Except for the specific purposes described in the Grant of Licence and the Licence Types sections, licence keys issued by SoftPerfect may not be distributed by any person, organisation or their agents without written permission from the copyright holder.
MODIFICATIONS
Unauthorised modification, decompilation or reverse engineering of the software or any subset of the software without written permission from the copyright holder is strictly prohibited.
USE
This software is distributed “as is”. No warranty of any kind is expressed or implied. You use it at your own risk. In no event shall SoftPerfect or its agents be liable for any loss or inaccuracy of data, loss or interruption of use, or cost of procuring substitute technology, goods or services, or any other loss or damages.
You may not use this software in connection with any illegal, fraudulent, infringing, harmful or offensive activity.
TERMS OF ACCEPTANCE
Installation or use of this software signifies your acceptance of the terms and conditions of the licence. If you do not agree with them, you must stop using and remove the software from your devices. SoftPerfect reserves all rights not expressly granted here.